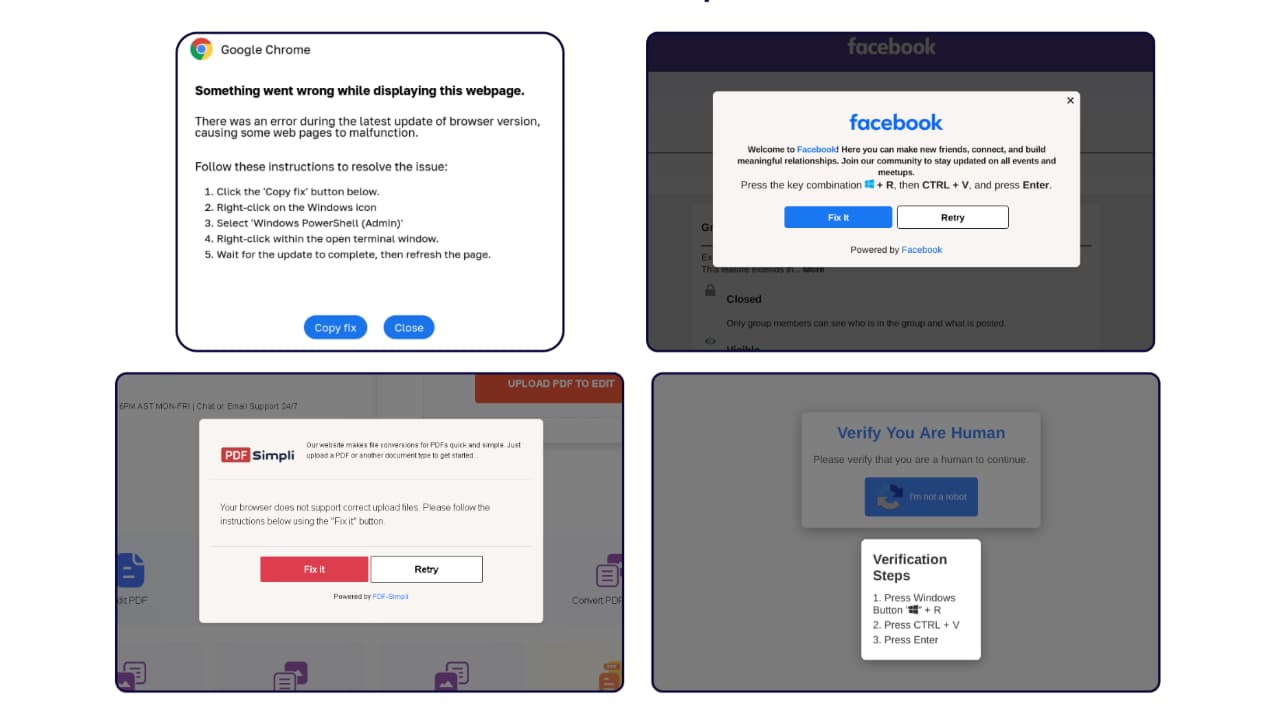
A new scam called ClickFix is targeting users and is on the rise in the US. As the name suggests, it prompts you to click on a link, claiming to fix an issue, but in reality, it infects your computer with malware. I reported on this earlier, detailing how threat actors used messages impersonating errors from Google Chrome, Microsoft Word, and OneDrive to infect users’ computers.
Now, a similar type of attack is affecting Google Meet users, regardless of whether they’re using a Windows PC or a Mac. I explain how this cyberattack works and what you can do to protect yourself.
GET SECURITY ALERTS, EXPERT TIPS – SIGN UP FOR KURT’S NEWSLETTER – THE CYBERGUY REPORT HERE

How the Google Meet trap works
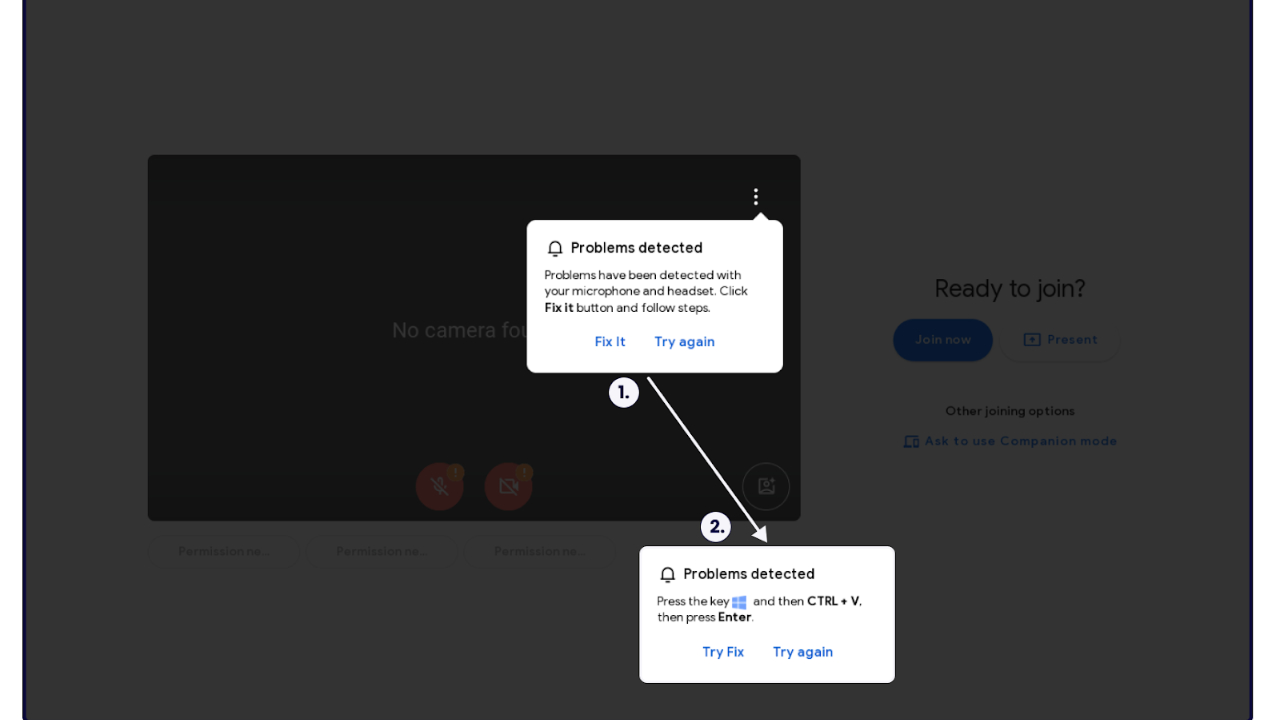
According to French cybersecurity company Sekoia, it all starts with an email containing a link to a Google Meet. The email can come from any address and may be socially engineered to look like it’s related to your organization. It could link to a Google Meet invite for a meeting, webinar, online collaboration, or something similar. When you click on the link, you’ll be directed to a fake Google Meet page, which will soon display a warning claiming there’s an issue with your PC. It might say your microphone or camera isn’t working or that there’s a problem with your headset.
You can expect to see the following URLs in these fake meeting emails:
meet[.]google[.]us-join[.]com
meet[.]google[.]web-join[.]com
meet[.]googie[.]com-join[.]us
meet[.]google[.]cdm-join[.]us
This fake page will also display a pop-up offering to fix the issue, showing phrases like ‘Press the key combination’ or ‘CTRL+V.’ When you follow these instructions, malicious code is pasted into the Windows prompt, infecting your computer with malware. Once the code is on your computer, hackers can gain access to your cryptocurrencies, sensitive files, and personal information.
Sekoia has uncovered several other malware distribution clusters beyond Google Meet. These include platforms like Zoom, PDF readers, fake video games (such as Lunacy, Calipso, Battleforge, and Ragon), web3 browsers and projects like NGT Studio, and messenger apps such as Nortex.
Sekoia
DON’T LET SNOOPS NEARBY LISTEN TO YOUR VOICEMAIL WITH THIS QUICK TIP
The bigger picture
Back in July, McAfee noticed that ClickFix campaigns were ramping up, especially in the US and Japan (via Bleeping Computer). Lately, two groups—Slavic Nation Empire (SNE) and Scamquerteo—have been behind some of these attacks. Both are said to be offshoots of larger crypto scam gangs, Marko Polo and CryptoLove.
Earlier this year, Proofpoint found that malware was spreading by pretending to be fake error messages for Google Chrome, Word, and OneDrive, tricking people into downloading malicious code. They also pointed out a method called “email lure,” where hackers send fake emails pretending to be from MS Word to infect computers.
Sekoia
BEST ANTIVIRUS FOR PCS, MACS, IPHONES AND ANDROIDS – CYBERGUY PICKS\
4 ways to protect yourself from harmful software
The fake Google Meet page creates a sense of urgency, making users click on the links and unknowingly compromise their devices. There are several steps you can take to protect yourself from such cyberattacks.
1) Have strong antivirus software: The best way to protect yourself from clicking malicious links that install malware that may get access to your private information is to have antivirus protection installed on all your devices. This can also alert you of any phishing emails or ransomware scams.
My top pick is TotalAV, and you can get a limited-time deal for CyberGuy readers: $19 your first year (80% off) for the TotalAV Antivirus Pro package.
2) Monitor your accounts: Regularly review your bank statements, credit card statements, and other financial accounts for any unauthorized activity. If you notice any suspicious transactions, report them immediately to your bank or credit card company.
3) Place a fraud alert: Contact one of the three major credit reporting agencies (Equifax, Experian, or TransUnion) and request a fraud alert to be placed on your credit file. This will make it more difficult for identity thieves to open new accounts in your name without verification.
4) Enable two-factor authentication: Enable two-factor authentication whenever possible. This adds an extra layer of security by requiring a second form of verification, such as a code sent to your phone, in addition to your password.
HOW TO REMOVE YOUR PRIVATE DATA FROM THE INTERNET
Kurt’s key takeaways
Hackers have come up with sneaky ways to trick you into installing malware. They use social engineering to make emails and website prompts look legit, hoping you’ll click on a link and follow their instructions. The best way to protect yourself is by avoiding unknown links and always checking the URL of the page you’re on before taking any action.
Have you ever received an email or prompt that looked suspicious but seemed legitimate at first glance? Let us know in the comments below.
FOR MORE OF MY SECURITY ALERTS, SUBSCRIBE TO MY FREE CYBERGUY REPORT NEWSLETTER HERE
Copyright 2024 CyberGuy.com. All rights reserved. CyberGuy.com articles and content may contain affiliate links that earn a commission when purchases are made.



1 comment
Kurt, I’m a senior software engineer with 40 plus years of experience. It is wonderful to educate people about cyber security. Thank you!