Google ads are mostly harmless, but if you see one promoting a particular web browser, avoid clicking. Security researchers have discovered new malware for Mac devices that steals passwords, cryptocurrency wallets, and other sensitive data. It masquerades as Arc, a new browser that recently gained popularity due to its unconventional user experience.
GET SECURITY ALERTS, EXPERT TIPS – SIGN UP FOR KURT’S NEWSLETTER – THE CYBERGUY REPORT HERE
Arc
How the Mac malware infects your device
The Mac malware lurks behind sponsored search results. Clicking the ad redirects you to arc-download[.]com, a phony website that pretends to offer a Mac version of Arc. The downloaded file looks like a typical Mac app installer.
However, there’s one catch— you’re asked to run the file by right-clicking and choosing open, rather than the more straightforward method of simply double-clicking on the file. This is to bypass a security measure Macs have in place. By forcing you to skip this step, the malware tricks you into installing it.
An analysis of the malware code shows that once installed, the stealer sends stolen information, such as your passwords, to the IP address 79.137.192.4, which turns out to be the home base for this malware’s control panel. This sneaky panel lets cybercriminals access stolen data from infected accounts.
“There is an active scene for Mac malware development focused on stealers,” Jérôme Segura, lead malware intelligence analyst at Malwarebytes, wrote. “As we can see in this post, there are many contributing factors to such a criminal enterprise. The vendor needs to convince potential customers that their product is feature-rich and has low detection from antivirus software.”
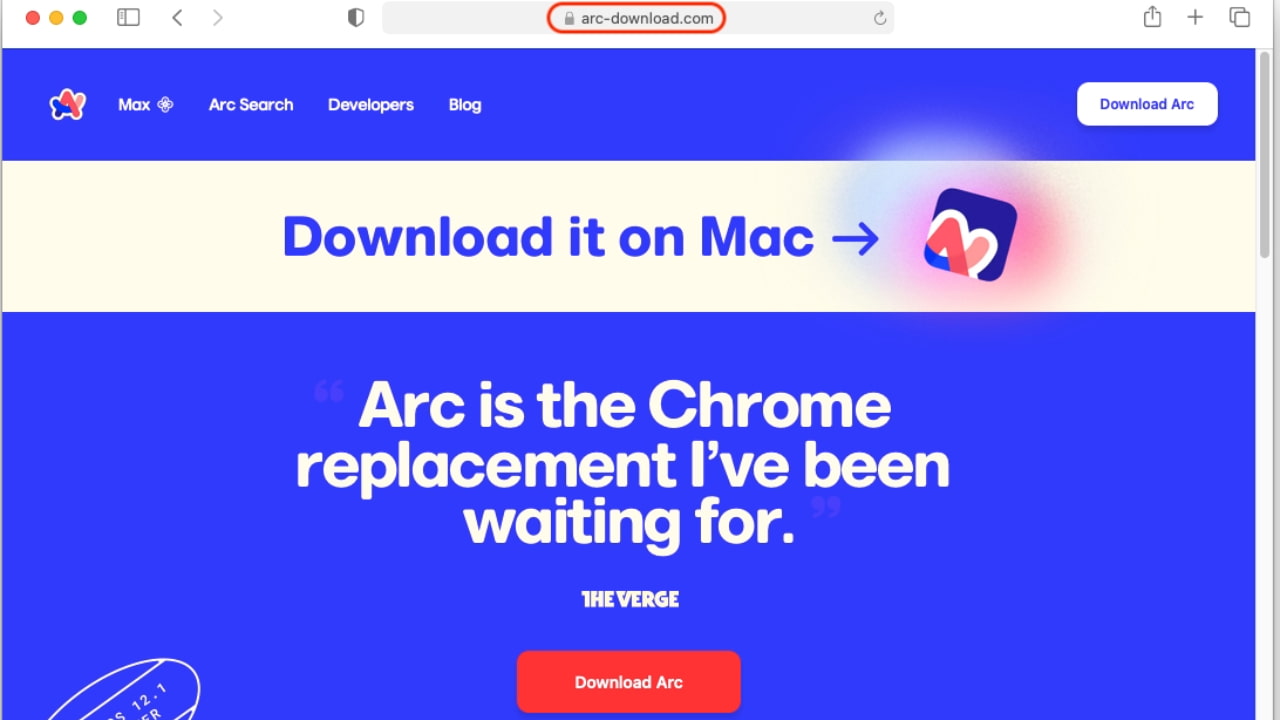
Malwarebytes
ANDROID BANKING TROJAN MASQUERADES AS GOOGLE PLAY TO STEAL YOUR DATA
The Mac malware is “verified by Google”
The Mac malware posing as a Google ad is called Poseidon, according to researchers at Malwarebytes. When clicking the “more information” option next to the ad, it shows it was purchased by an entity called Coles & Co, an advertiser identity Google claims to have verified.
Google verifies every entity that wants to advertise on its platform. In Google’s own words, this process aims “to provide a safe and trustworthy ad ecosystem for users and to comply with emerging regulations.” However, there seems to be some lapse in the verification process if advertisers can openly distribute malware to users. Though it’s Google’s job to do everything it can to block bad ads, sometimes bad actors can temporarily evade their detection.
This isn’t even the first instance of cyber criminals exploiting Google ads. I reported in May that ads are being used to position bogus websites atop your search results. These websites pose as trustworthy sites, and they pilfer your money and personal information.
In this latest instance, Google identified this issue and suspended the advertiser account for violating its policies, removing all its ads from its platforms, even before the Malwarebytes report.
We reached out to Google, and a spokesperson offered this statement:
We prohibit ads that attempt to circumvent our enforcement by disguising the advertiser’s identity to deceive users. When we identify ads that violate our policies we move quickly to remove the ads and suspend the associated advertiser account when applicable, as we did in this case.
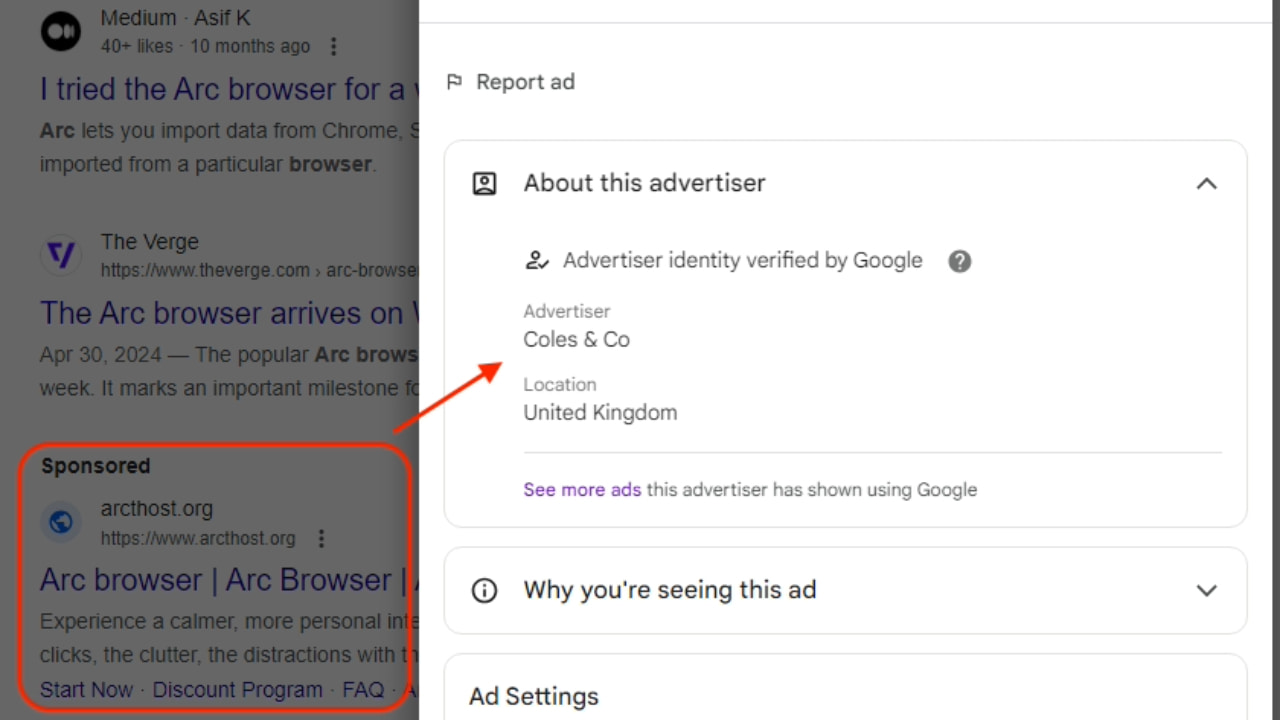
Malwarebytes
ANDROID USERS AT RISK AS BANKING TROJAN TARGETS MORE APPS
5 ways to protect yourself from Google ads malware
It’s hard to detect which Google ad is malicious. Follow these 5 tips to protect yourself from these Google search scams.
1) Bookmark or save URL: If you frequently visit certain sites, particularly social media and financial platforms, bookmark or save their URLs. This will ensure that you end up on the right page and avoid counterfeit pages.
2) Avoid clicking on unknown links: Always type the website address directly into your browser’s address bar. Avoid clicking on links, especially those sent via email or found on unfamiliar websites, as they might lead to counterfeit or malicious pages. By manually entering the URL, you ensure that you’re navigating to the correct and intended site, reducing the risk of phishing attacks and other online threats.
The best way to protect yourself from clicking malicious links that install malware that may get access to your private information is to have strong antivirus protection installed on all your devices. This can also alert you of any phishing emails or ransomware scams.
My top pick is TotalAV, and you can get a limited-time deal for CyberGuy readers: $19 your first year (80% off) for the TotalAV Antivirus Pro package.
3) Download apps from trusted platforms: When downloading apps on your Mac or any other Apple device, use the App Store. Apple has strict security guidelines that only allow secure and legitimate apps to be hosted on its platform.
4) Keep your browser updated for maximum security: Regularly updating your browser is crucial, as updates often include security patches that protect against newly discovered vulnerabilities.
5) Recognize urgent requests as potential scams: Always be wary if someone is urgently requesting you to do something like send money, provide personal information, or click on a link—chances are it’s a scam.
HOW TO REMOVE YOUR PRIVATE DATA FROM THE INTERNET
Kurt’s key takeaway
The Poseidon malware case is a wake-up call for everyone to be super careful with online ads, especially those for popular software. Don’t just click on the first sponsored search result that pops up. Also, ensure you only download apps from trusted sources, like official app stores. To add another layer of security, consider using strong antivirus protection.
Do you feel confident in recognizing legitimate download sites versus fake ones? Let us know in the comments below.
FOR MORE OF MY SECURITY ALERTS, SUBSCRIBE TO MY FREE CYBERGUY REPORT NEWSLETTER HERE
Copyright 2024 CyberGuy.com. All rights reserved. CyberGuy.com articles and content may contain affiliate links that earn a commission when purchases are made.


