Curious about the security of your documents in the cloud? You’re not alone. We recently received an email from Dana in Marietta, GA, who is asking this,
I just read your article on saving documents to the cloud. What is your opinion on protecting those documents by encrypting them first? Does that prevent companies like Google from harvesting them? Also, how are these files removed after the death of the individual?” – Dana, Marietta, GA
Wonderful question, Dana. Data encryption can be an overwhelming concept at first, but when broken down, it is simple.
Encryption is a process of transforming data into an unreadable form that can only be accessed by authorized parties with the decryption key, which is basically just a password that can turn the data back into text that can be read and used.
This makes it nearly impossible for anyone without access to steal, change, or compromise whatever you are protecting. You may choose to do this to protect sensitive files like financial or medical documents.
However, encryption does not guarantee complete privacy. Some companies, like Google, may have access to your encryption keys or use other methods to decrypt your data.
Therefore, encrypting your documents may not prevent Google from harvesting them, depending on how you use their services and what their policies are.
What are the benefits of cloud encryption?
The main appeal of cloud encryption is improved cybersecurity. Encrypting your documents before uploading them to the cloud can provide an extra layer of protection against unauthorized access, data breaches, hacks, malware, and cyberattacks.
If or when data breaches occur on a site with your information, your data is much more likely to be safe if encrypted.
MORE: DON’T FALL FOR THIS NEW ROUND OF ICLOUD SUPPORT SCAM EMAILS
Should you encrypt your data before sending it to the cloud?
You can add an extra layer of security by encrypting your data yourself before sending it to the cloud. While most cloud services do encrypt your data automatically, they do so in a way that isn’t the safest or most private.
They can still read your data, and if a hacker manages to get into the server with your data, they can read it as well.
There are many really good third-party encryption apps that allow you to encrypt individual or large groups of files.
There are also built-in encrypting methods on both Windows and Mac. These methods can also help you password-protect certain important documents and files, like financial records or personal information.
How to encrypt on Windows
- Right-click on the folders you want to encrypt and go to properties
- Choose advanced under the general category
- Tick “Encrypt content to secure data”*
- Click Ok and then Apply
- Select “apply changes to folder, sub folder, and files”
- Back up the file encryption key and store it safely
If you are encrypting only a single file, and not a folder, it’s just as easy.
- Right-click on the file you want to encrypt and go to properties
- Choose advanced under the general category
- Tick “Encrypt content to secure data”
- Click OK and then Apply
- Select “Encrypt the file and its selected folder
- Back up the file encryption key and store it safely
*Please note the “Encrypt contents to secure data” option is only available in Windows 11 Pro, Enterprise, and Education editions. If you’re using Windows 11 Home, this feature won’t be available. You may consider using third-party encryption tools like BitLocker (if available on your edition). BitLocker is a great tool for encrypting your data and ensuring its security
How to encrypt on Mac
This one is a bit more complicated and reserved for our more technically brave. If you are unsure about this process, you may want to try the following using dummy or test folders and files first.
- To begin with, please note that you can only encrypt folders which then protect the files within them.
- Create a folder on your desktop by right-clicking and selecting Create a new folder. Feel free to put any documents you may have in there.
- In the top left bar on your desktop, select Go, then scroll down and select Utilities.
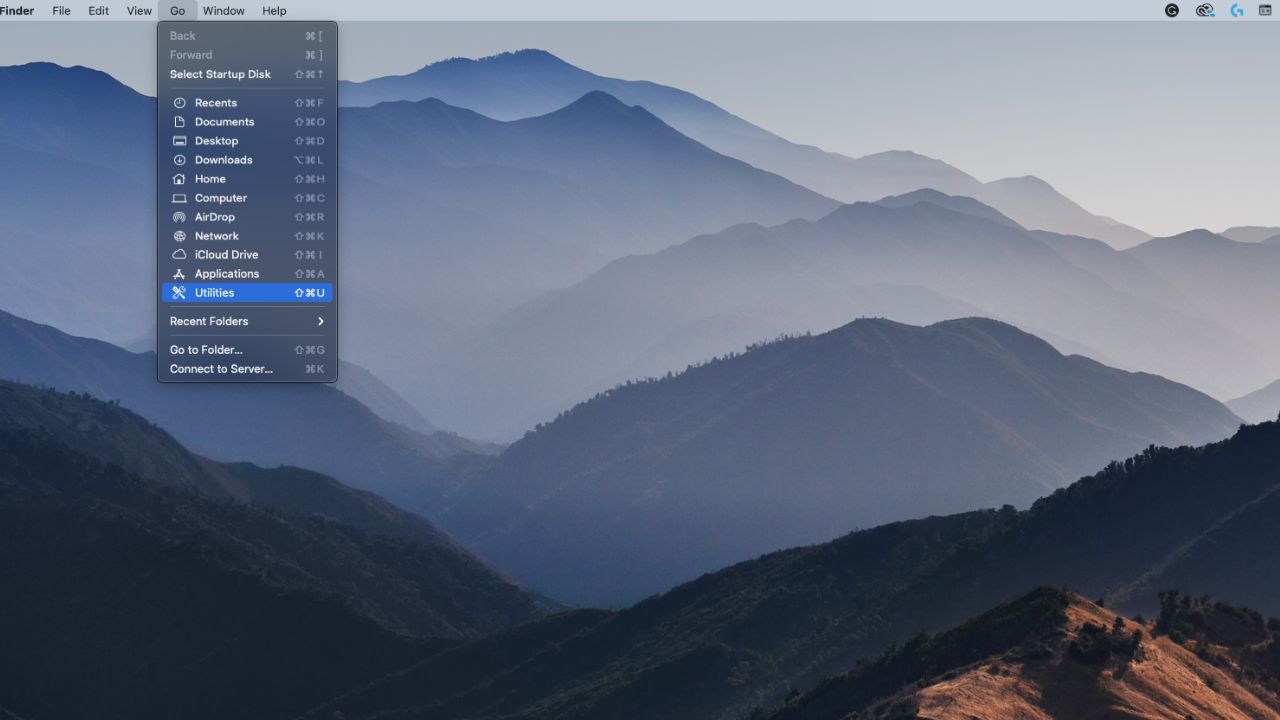
- Open Disk Utility
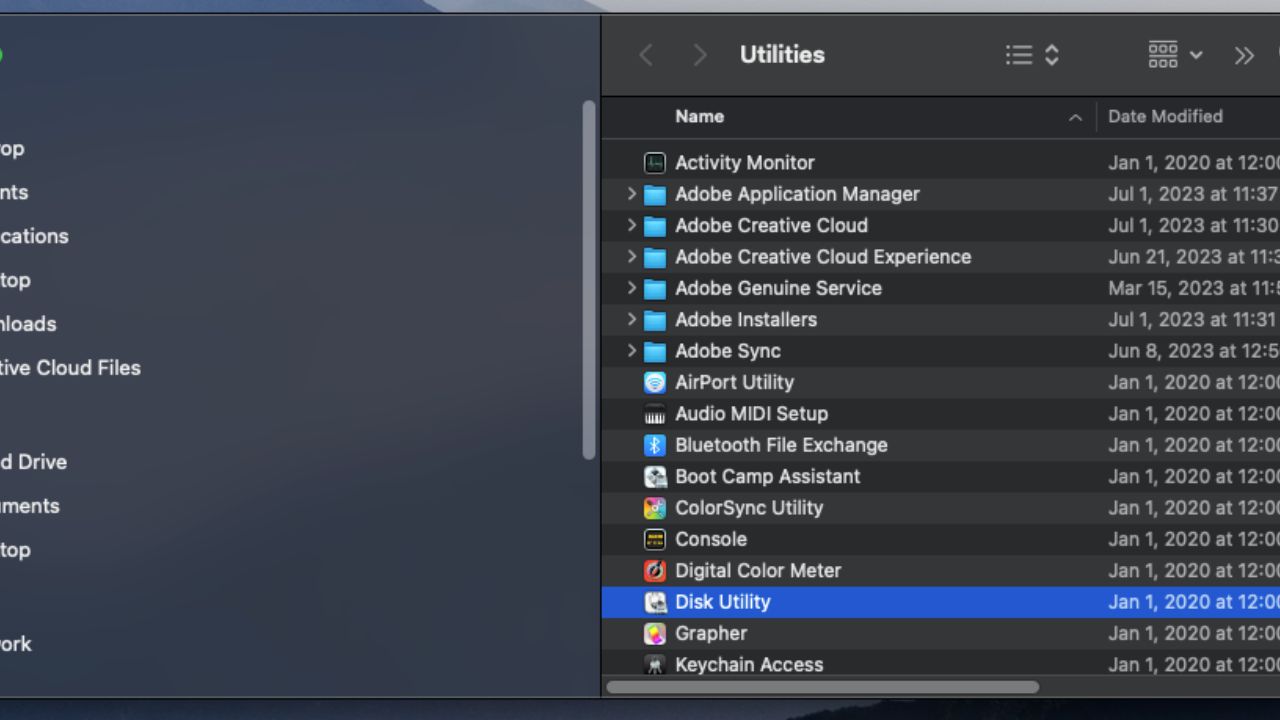
- In the top left bar, go to File, then New Image right beneath it, and then Image from Folder

- Find and select the folder you created
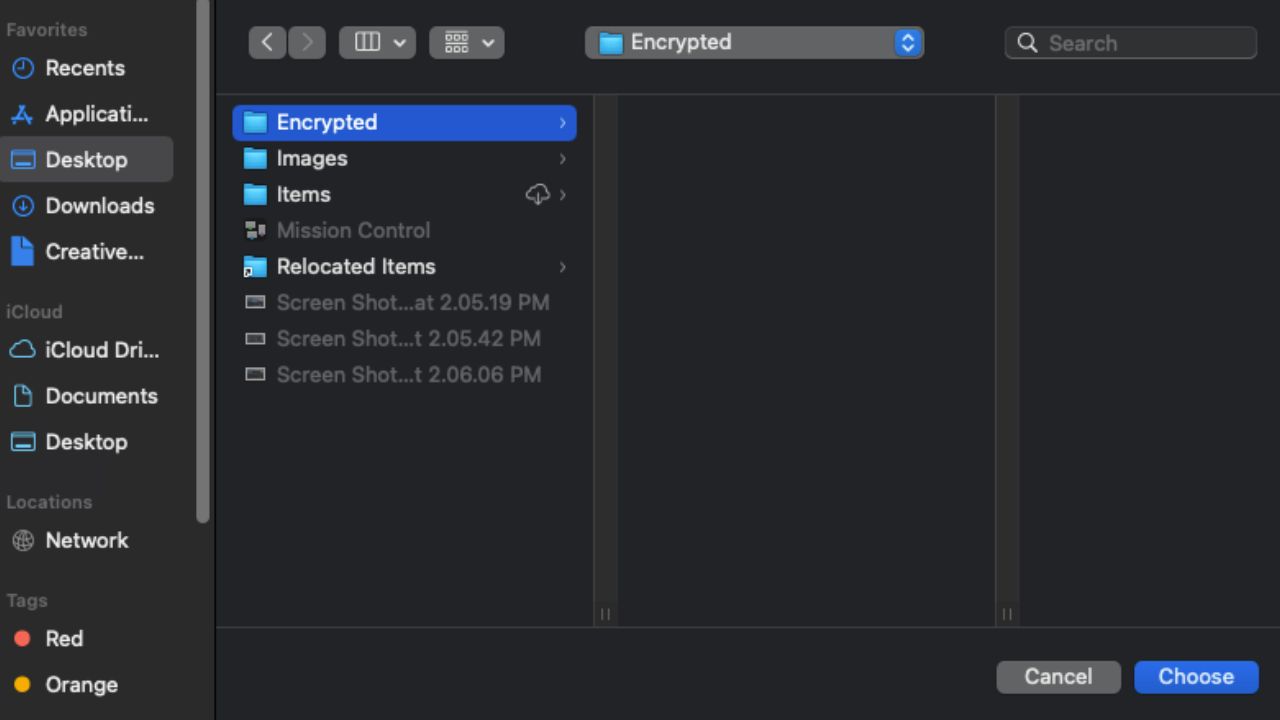
- Click Choose
- Click on Encryption pulldown and choose 128-bit AES encryption
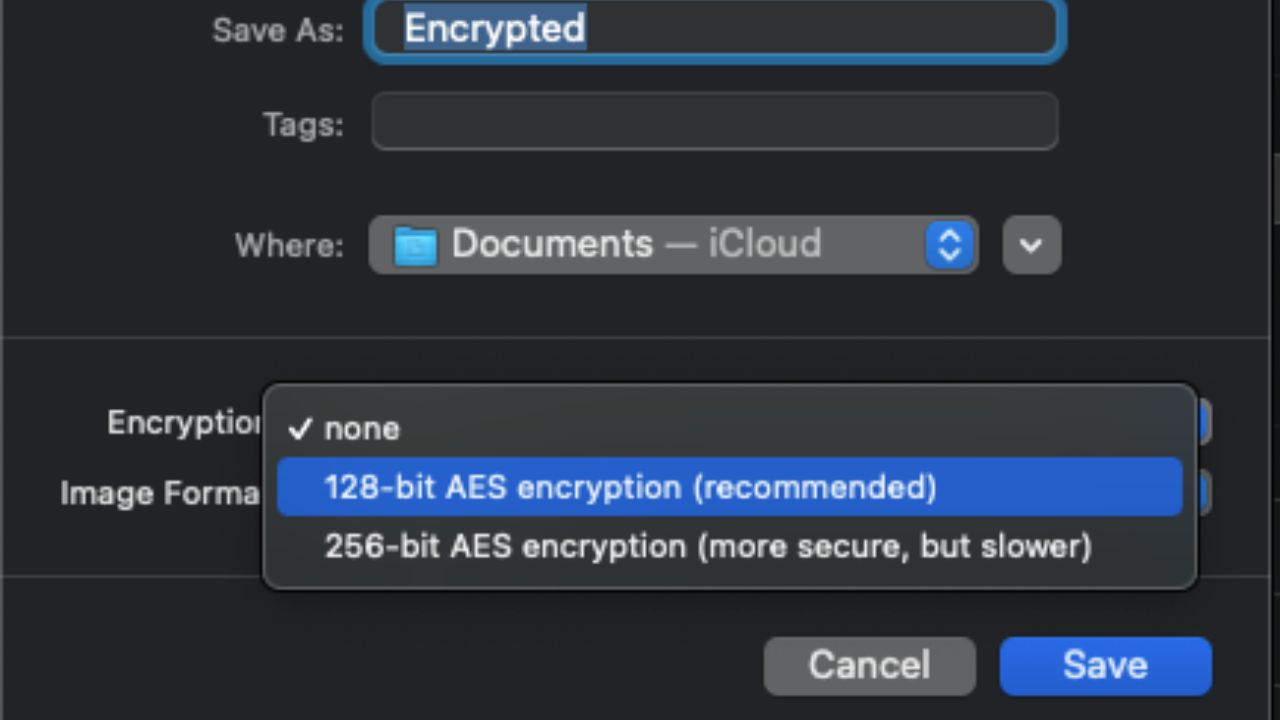
- Create a strong password and verify it by typing it in again. Then click choose.
- Select the Image Format pulldown
- If you want to be able to edit the file, select read/write; if you do not need to edit the file, select compressed
- Click Save
- Click Done
An encrypted copy of the file will be created in your preferred destination. However, the original, unencrypted folder will remain.
Now what should you do?
![]()
The now encrypted file will have the extension .dmg at the end of it.
To test it, try double-clicking it to open.
When you attempt to open the file by double-clicking it, it will ask you for the password you just set to open the now encrypted file. After doing so, a “disk” with the same name will be created, which you can now find under the “Locations” area in your finder.
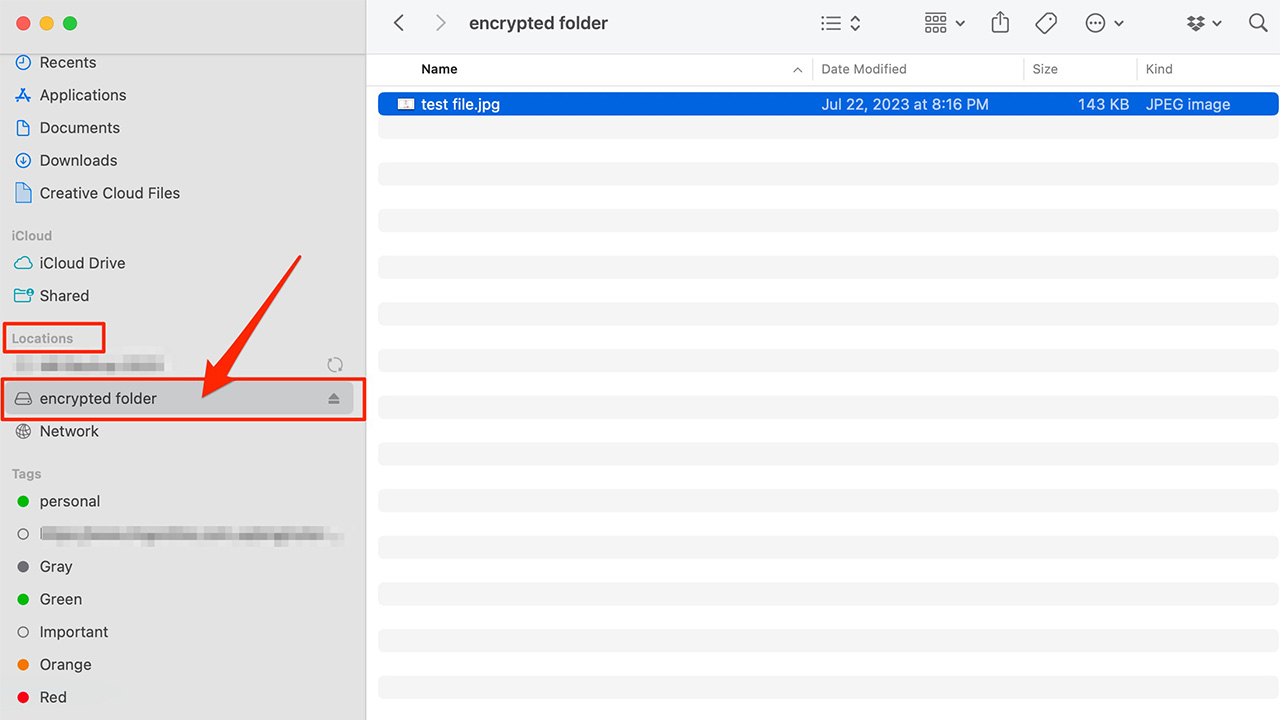
After testing this out and opening it, for maximum security, it is recommended you move the original folder to the trash bin wherever you have it on your desktop. Then, click on the trash can, and select Empty Trash. Remember, after you do this, you won’t be able to retrieve the files. Be sure you have the password you just put into your password manager or written down in a good place.
Now, you will only have the encrypted file remaining.
Amp up the security of your iCloud data
Let’s say you really want to amp up the security of your iCloud data. Apple has got you covered with its Advanced Data Protection for iCloud, which is its top-tier cloud data security feature. This is an optional setting that takes your iCloud data security to the next level.
When you turn it on, most of your iCloud data, such as your Photos, Notes, iCloud Backup, and more, gets locked up with end-to-end encryption. This means nobody, not even Apple, can access your encrypted data.
Requirements before setting up Advanced Data Protection
There are a number of requirements that you’ll need to be aware of before you turn on Advanced Data Protection.
- Updated software on all of your devices that you are signed into with your Apple ID
- A password or passcode set for your Apple device
- An Apple ID with two-factor authentication
- At least one account recovery contact or recovery key. Don’t already have one? No problem. Apple will help you set one up when you turn on Advanced Data Protection on your device.
Set up an alternative recovery method
Now, before you enable Advanced Data Protection for iCloud, you’ll also need to set up an alternative recovery method, either a recovery contact or recovery key.
This is important because, with Advanced Data Protection, Apple won’t have the keys to unlock your encrypted data if you ever need to recover it.
So you’ll rely on one of your recovery methods, like your device passcode or password, your recovery contact, or your recovery key, to regain access to your iCloud data if you ever get locked out.
How to turn on Advanced Data Protection for iCloud
To activate Advanced Data Protection, it requires an iPhone running IOS 16.2, an iPad running OS 16.2, or a Mac running macOS 13.1.
On iPhone or iPad
- Open the Settings app
- Tap your name, then tap iCloud
- Scroll down, tap Advanced Data Protection, then tap Turn on Advanced Data Protection
- Then, follow the onscreen instructions to review your recovery methods and enable Advanced Data Protection
On Mac
- Choose the Apple Menu and then tap System Settings
- Click your name, then tap iCloud
- Click Advanced Data Protection, then click Turn on
- Then, follow the onscreen instructions to review your recovery methods and enable Advanced Data Protection
ARE YOU PROTECTED? SEE THE 2023 BEST ANTIVIRUS PROTECTION WINNERS
What are the downsides to encryption?
Everything you encrypt becomes useless without the digital key. If you have many items encrypted in many different places, it can be hard to safely store or remember all of your different codes. In addition, if somehow the key is lost, forgotten, corrupted, or destroyed, there is no way to gain access to your information.
It is also important to realize that no security is completely impenetrable. While unlikely, there is a possibility that an outside source cracks your encryption key. The whole concept and doing it manually can be pretty complicated too.
Benefits of a password manager
One of the key ways to protect your data as you encrypt your documents is through the use of a password manager.
It will help you to create unique and difficult-to-crack passwords that a hacker could never guess. It also keeps track of all your passwords in one place so that you never have to remember them yourself.
The fewer passwords you remember, the less likely you will be to reuse them for your accounts.
Check out my best expert-reviewed password managers of 2023 here
What to do so loved ones can access your files and data after death
Some providers may delete your files after a period of inactivity, while others may allow you to designate a beneficiary or a digital executor who can access your files after your death.
It is important to ensure your data or the data of your loved ones, is left in safe hands. There are a few different ways to ensure this.
Apple, for example, has created a “legacy contact” system where the user can create an access key. They can then give this key, either digitally or on paper, to others to use in conjunction with a copy of their death certificate to access their data after death. Here’s how to set it up:
To set up a legacy contact on a Mac, click here. To set up a legacy contact on a PC or Android, click here.
MORE: HOW TO BE REMEMBERED FOREVER ON FACEBOOK
What to do so loved ones can access your files on Google after death
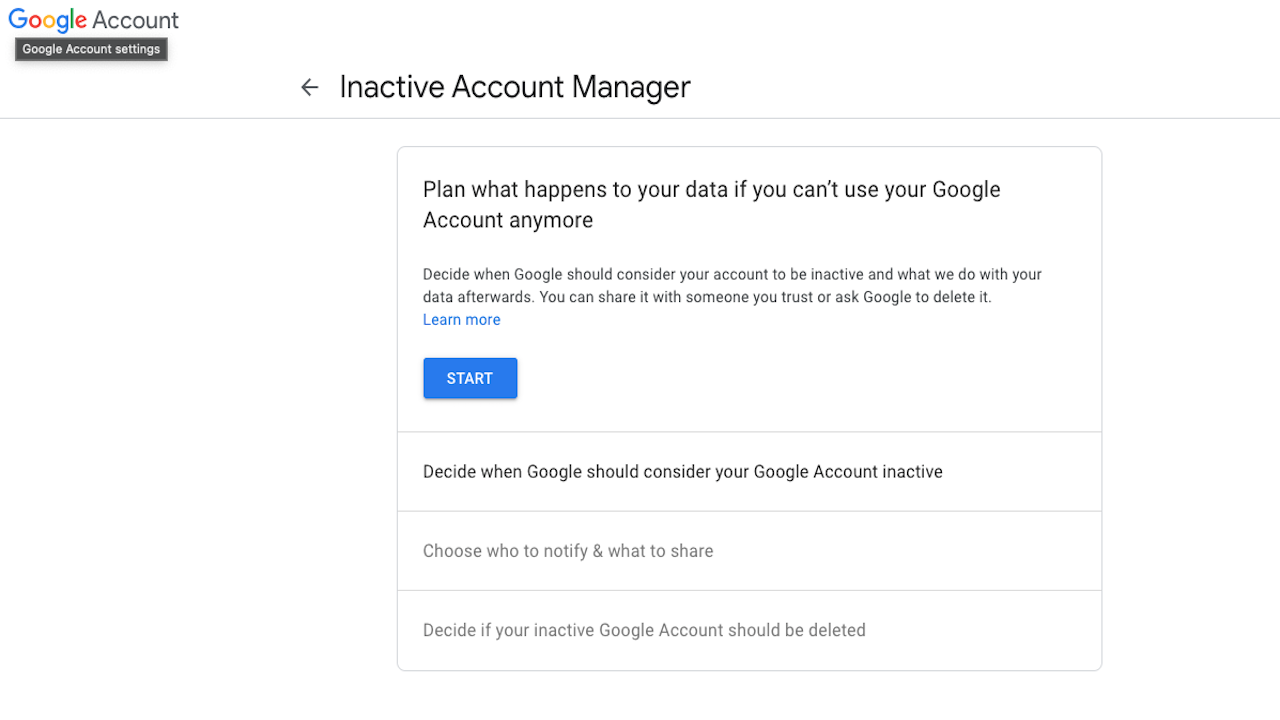
Google lets the user set up an “Inactive account manager.” This account will automatically contact the people you list after you have been inactive from your Google account for a chosen period of time. Here’s how to set it up:
- Select this link
- Click Start
- Select the pencil icon to choose how long you want the period of inactivity to be
- Click Save
- Next, click ADD PHONE NUMBER and then type in your own phone number,
- If it sends you a verification code, enter in the given code, and click VERIFY, then click NEXT on the bottom
- Then select ADD PERSON and add the email of who you want to be contacted and select NEXT
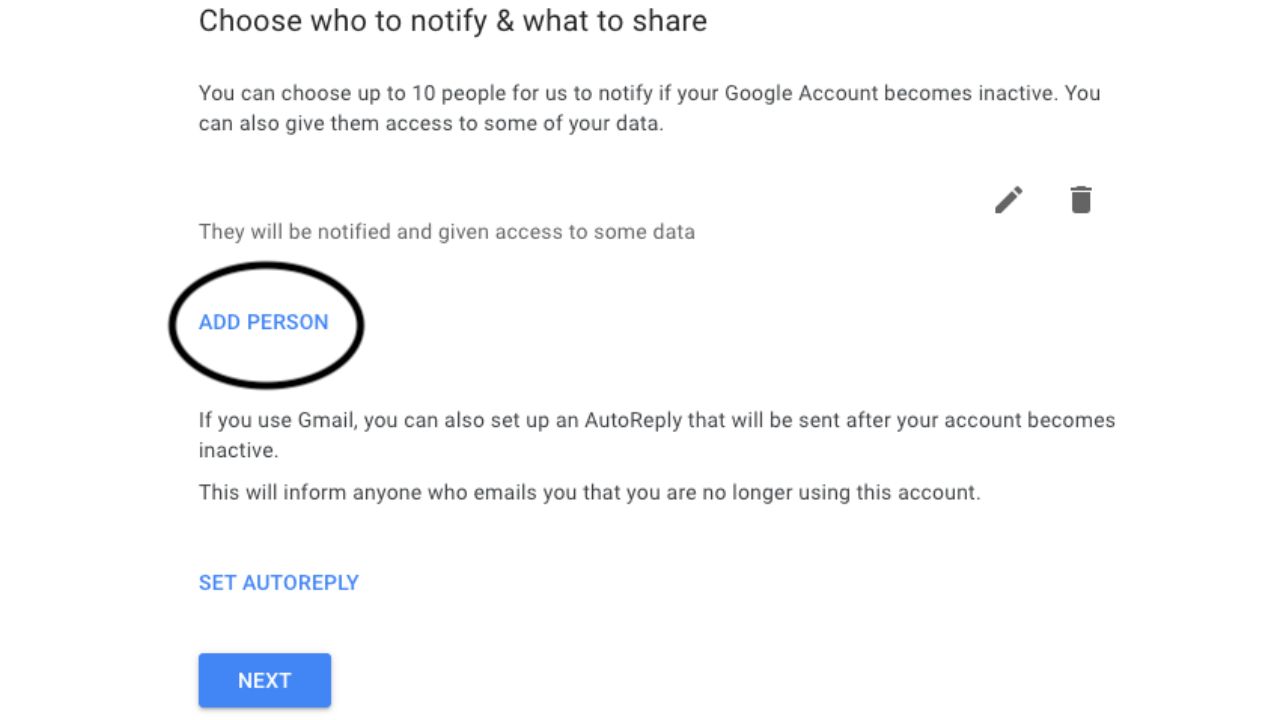
- Check the boxes of which data you want shared with the person, click NEXT, and add their phone number and click SAVE
- Repeat these steps for whoever else you want to have access
- Click NEXT at the bottom
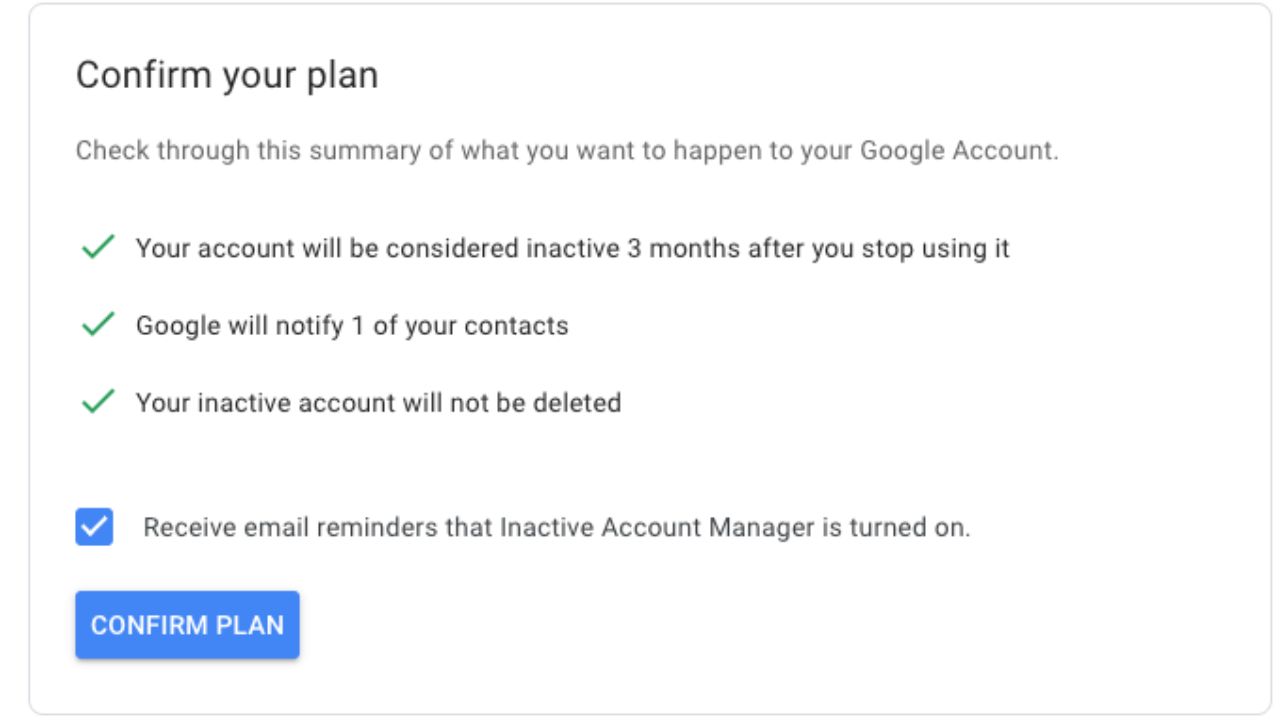
- Select if you want your Google account to be deleted after death by ticking the switch, turning it blue
- Click REVIEW PLAN and then CONFIRM PLAN if you are satisfied
Other methods to keep information and accounts safe after death
There are also alternative measures that can be taken to keep your information safe, even after death. Some password managers, like 1Password, for example, have you create an Emergency Kit when you sign up, which includes all the information someone would need to log into your account. Print it out or download a copy to a USB drive and place it somewhere safe, like a lock box, where your loved ones can access it in the event of your death.
How do you feel about encrypting your documents before uploading them to the cloud? Are you prepared to ensure your data is accessible to close friends or family members after you pass away? Let us know by commenting below.
FOR MORE OF MY TECH TIPS AND SECURITY ALERTS, SUBSCRIBE TO MY FREE CYBERGUY REPORT NEWSLETTER HERE


