A new malware has been detected by security researchers that is suspected of conducting espionage. Hackers infect devices by impersonating government agencies, usually tax agencies such as the Internal Revenue Service (IRS). Once the malicious software is on a PC, it can gather intelligence (collecting personal data, passwords, and more), download additional malicious software, and upload data to the hacker’s server. It does all this while using Google Sheets to avoid suspicion and store data.
GET SECURITY ALERTS, EXPERT TIPS – SIGN UP FOR KURT’S NEWSLETTER – THE CYBERGUY REPORT HERE

It all starts with a fake email
The hackers behind the malware, called “Voldemort,” have cleverly designed it to avoid getting caught. Just like the name Voldemort spelled trouble in J.K. Rowling’s Harry Potter series, it’s causing issues in the cybersecurity world too.
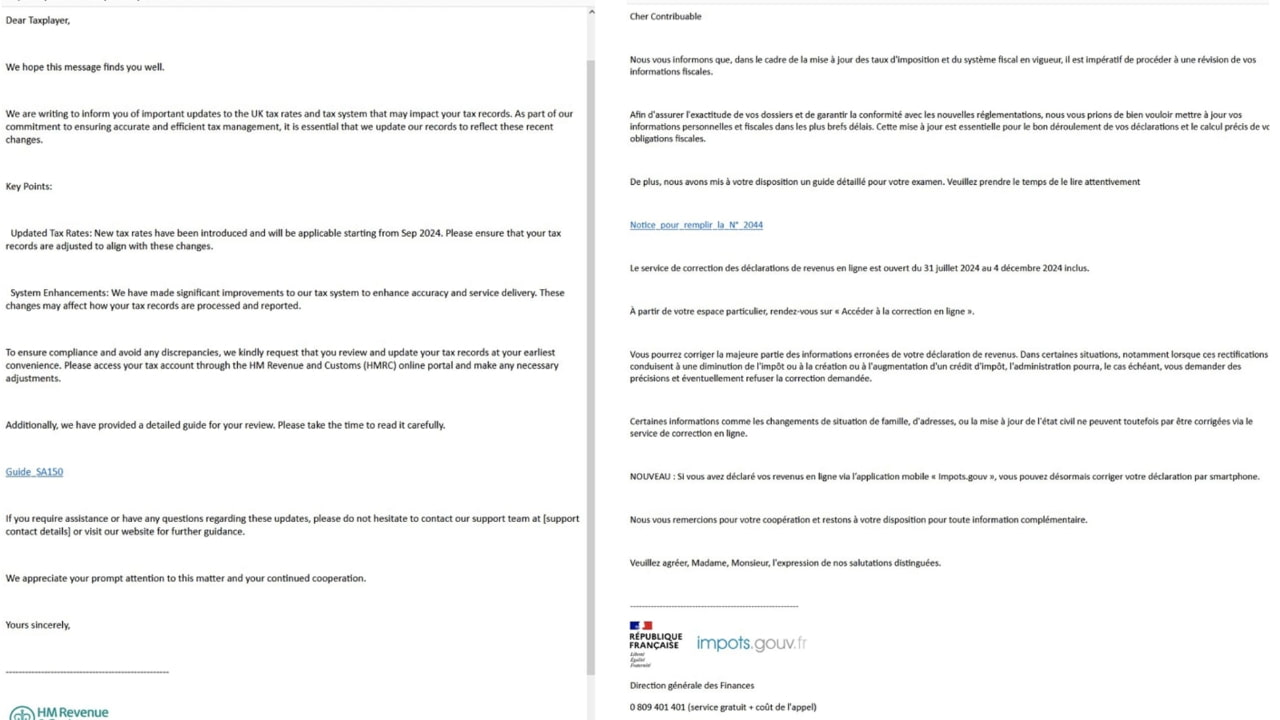
The cyber attack kicks off when you receive an email that looks like it’s from a government tax agency. According to Proofpoint, the hackers behind this campaign have been impersonating tax agencies in various countries, including the U.S. (IRS), the UK (HM Revenue & Customs), France (Direction Générale des Finances Publiques), Germany (Bundeszentralamt für Steuern), Italy (Agenzia delle Entrate), and, as of August 19, India (Income Tax Department) and Japan (National Tax Agency). Each email lure was customized and written in the language of the tax authority being impersonated.
Proofpoint analysts found that the hackers tailored their phishing emails to match the target’s country of residence based on publicly available information rather than the organization’s location or the language suggested by the email address. For example, some targets in a European organization received emails impersonating the IRS because they were linked to the U.S. in public records. In some cases, the hackers mixed up the country of residence when the target shared a name with a more prominent individual.
The email also tries to mimic the email of the government agency. For example, the US folks were sent fake emails using “no_reply_irs[.]gov@amecaindustrial[.]com”.
Credit: Proofpoint
HEARTLESS SCAMMERS ARE PREYING ON PEOPLE’S LOST PET ANGUISH
The attack cleverly unfolds on your device
In the fake email, hackers impersonating the government warn you about changes in the tax rates and tax systems and ask you to click a link to read a detailed guide. Clicking on the link brings you to a landing page, which uses Google AMP Cache URLs to redirect you to a page with a “Click to view document” button.
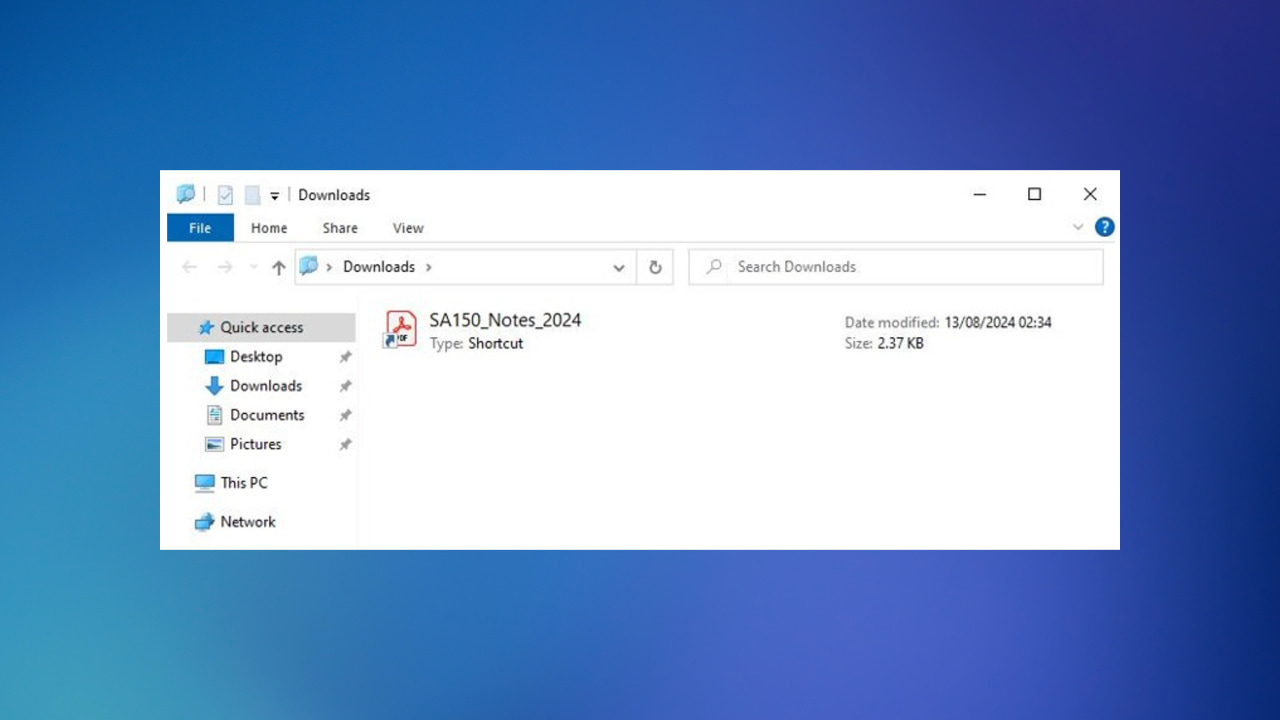
After you click the button, the hackers check if you’re using a Windows device. If you are, you’ll be redirected to another page. When you interact with that page, it triggers a download that looks like a PDF file in your PC’s download folder, but it’s actually an LNK or ZIP file hosted on an external server.
When you open the file, it runs a Python script from another server without actually downloading the script to your computer. This script collects system information to profile you, while a fake PDF opens to hide the malicious activity.
Credit: Proofpoint
MOST TARGETED CITIES FOR TRAVEL BOOKING SCAMS
Voldemort uses Google Sheets to store data
Once the malware has successfully infected your Windows device, it can:
- Ping: Check if it’s still connected to its control server.
- Dir: Get a list of files and folders on your system.
- Download: Send files from your system to the control server.
- Upload: Put files from the control server onto your system.
- Exec: Run specific commands or programs on your system.
- Copy: Copy files or folders on your system.
- Move: Move files or folders around on your system.
- Sleep: Pause its activity for a set time.
- Exit: Stop running on your system.
The malware uses Google Sheets as its command center, where it gets new instructions and stores stolen data. Each infected device sends its data to specific cells in the Google Sheet, marked by unique IDs to keep everything organized.
Voldemort interacts with Google Sheets through Google’s API, using an embedded client ID, secret, and refresh token stored in its encrypted settings. This method gives the malware a reliable way to communicate without raising suspicion since Google Sheets is widely used in businesses, making it hard for security tools to block it.
HOW TO RECOGNIZE AND AVOID BEING A VICTIM OF VACATION RENTAL SCAMS
4 ways to protect yourself from malware attacks
Hackers are releasing increasingly sophisticated malware, but that doesn’t mean you’re defenseless. Below are some tips to help protect yourself from such attacks.
1) Read sensitive emails carefully: The best way to spot fake emails that deliver malware is to check them carefully. While hackers may be tech-savvy, their language skills often aren’t perfect. For example, in the screenshots above, you can see typos like “Taxplayers” instead of “Taxpayers.” Government agencies don’t usually make these kinds of mistakes.
2) Check email domain: Verify that the email domain matches the organization it claims to represent. For example, an email from the IRS should come from an address ending in “@irs.gov.” Be cautious of slight misspellings or variations in the domain.
3) Invest in data removal services: Hackers target you based on your publicly available information. That could be anything from your leaked info through a data breach to the information you provided to an e-commerce shop.
A service like Incogni can help you remove all this personal information from the internet. It has a very clean interface and will scan 195 websites for your information and remove it and keep it removed.
Special for CyberGuy Readers (60% off): Incogni offers A 30-day money-back guarantee and then charges a special CyberGuy discount only through the links in this article of $5.99/month for one person (billed annually) or $13.19/month for your family (up to 4 people) on their annual plan and get a fully automated data removal service, including recurring removal from 190+ data brokers. You can add up to 3 emails, 3 home addresses and 3 phone numbers (U.S. citizens only) and have them removed from data-broker databases.
I recommend the family plan because it works out to only $4.12 per person per month for year-round coverage. It’s an excellent service, and I highly recommend at least trying it out to see what it’s all about.
Get Incogni for your family (up to 4 people) here.
4) Have strong antivirus software: If you have strong antivirus software installed on your device, it can protect you when you receive these types of scam emails or accidentally open the attachment or click a link. The best way to protect yourself from clicking malicious links that install malware that may get access to your private information is to have antivirus protection installed on all your devices. This can also alert you of any phishing emails or ransomware scams.
My top pick is TotalAV, and you can get a limited-time deal for CyberGuy readers: $19 your first year (80% off) for the TotalAV Antivirus Pro package.
Kurt’s key takeaway
While researchers can’t say for sure, many of the techniques used by the malware are similar to those employed by hackers suspected of espionage. Even if this assessment turns out to be incorrect, the scale and sophistication of the attack are concerning. Anyone without technical knowledge could easily fall victim and lose personal data and money. This attack specifically targets Windows users, which also raises questions about Microsoft’s security framework.
What measures do you think organizations should implement to better protect individuals from malware attacks? Let us know in the comments below.
FOR MORE OF MY TIPS, SUBSCRIBE TO MY FREE CYBERGUY REPORT NEWSLETTER HERE
Copyright 2024 CyberGuy.com. All rights reserved. CyberGuy.com articles and content may contain affiliate links that earn a commission when purchases are made.


