If you use a Mac, you may have seen some pop-ups or notifications urging you to update your web browser. But before you click on them, you should know that they could be part of a malicious malware campaign called ClearFake, which is designed to steal your personal data.
What is ClearFake?
ClearFake is the name given to a malware campaign that uses fake browser updates to infect your Mac with a credential stealer called Atomic Stealer. This campaign was first discovered by security company Malwarebytes in their threat research report. According to Malwarebytes, ClearFake is one of the first social engineering campaigns that targets both Windows and Mac users with fake browser updates.
Credit: Malwarebytes
MORE: 35 BEST CYBER MONDAY DEALS
How ClearFake tricks you into installing Atomic Stealer on your Mac
The ClearkFake campaign uses compromised websites to redirect you to a landing page that looks very realistic and mimic the official website of Google Chrome or Safari. The landing page tells you that your browser is outdated and that you need to download the latest version. However, the download link is actually a DMG file that contains Atomic Stealer.
If you download and open the DMG file, you will see a fake installer that asks you to enter your administrative password. This is how the malware gets permission to run commands on your Mac and enable its stealing capabilities. The malware then collects your data and sends it to a command and control server that is controlled by the hackers behind the ClearFake campaign.

Credit: Malwarebytes
What is Atomic Stealer?
Atomic Stealer is a type of malware that targets Mac OS devices and can access your credentials, cookies, browser history, and sensitive files. It can also capture your screen and record your keystrokes. It is one of the most advanced and stealthy stealers for Mac OS, and it is sold on underground forums for a high price. Atomic Stealer is not a new threat, but it has a new way of infecting your Mac: through fake browser updates.
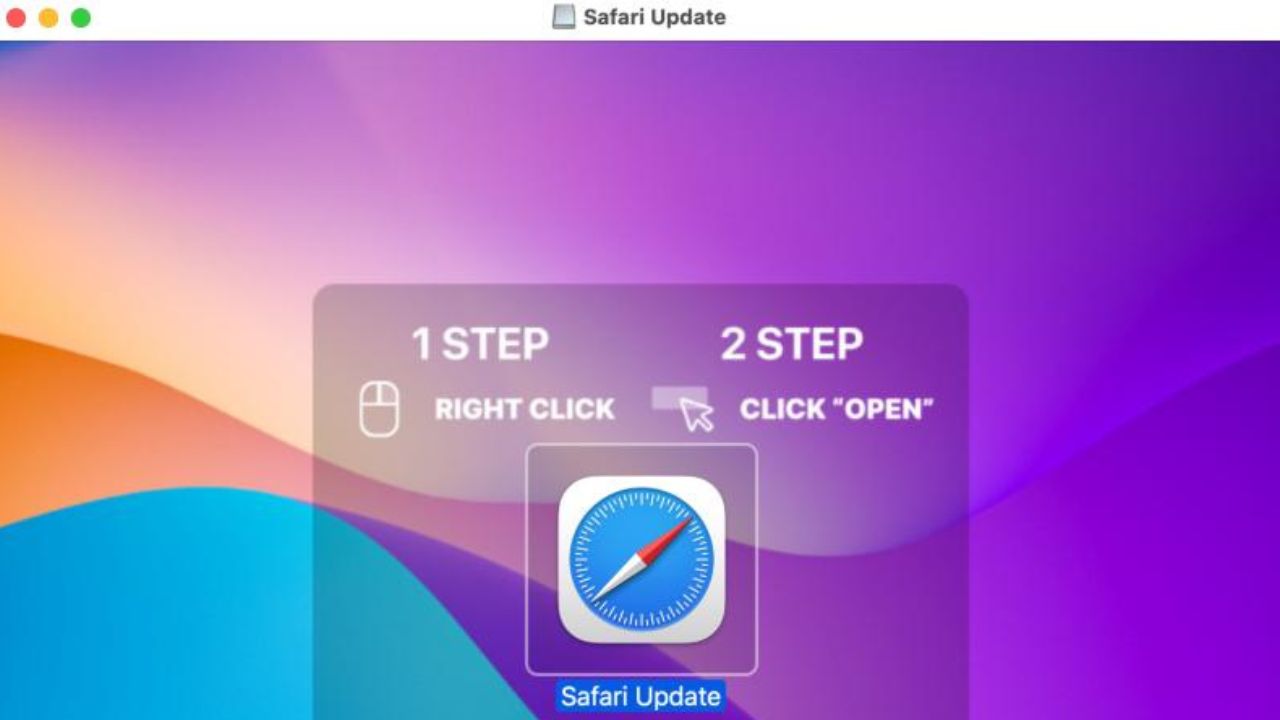
Credit: Malwarebytes
Did you accidentally download this software to your device? What to do.
If you suspect that your device has been infected with ClearFake malware, you can follow the steps below to check for its presence and remove it:
- Run a malware scan: Use your antivirus software to run a full system scan. This will help detect and remove any malicious files or programs on your device.
- Check your browser extensions: ClearFake malware is known to install browser extensions that can redirect your web traffic to malicious sites. Check your browser extensions and remove any suspicious ones.
- Check your downloads folder: ClearFake malware is often delivered through fake browser updates. Check your downloads folder for any suspicious files or programs that you may have downloaded unknowingly.
- Update your software: Keep your operating system and software up-to-date to ensure that you have the latest security patches and bug fixes.
- Change your passwords: If you suspect that your credentials have been compromised, change your passwords immediately.
How to protect yourself from ClearFake and Atomic Stealer?
To protect yourself from these threats, you should follow these steps:
Use a reliable antivirus software and keep it updated. Antivirus software can detect and remove malware from your device and prevent them from infecting your system. You should actively keep antivirus running in the background on your devices, scan your devices regularly and update your antivirus software to the latest version.
Holiday Special for CyberGuy Readers: My #1 pick is TotalAV, and you can get a limited-time deal for CyberGuy readers: $19 your first year (80% off) for the TotalAV Antivirus Pro package.
See our review of the Best Antivirus Protection of 2023 here.
Avoid clicking on suspicious links or attachments. Phishing emails and websites can look very convincing, but they may contain malicious links or attachments that can infect your device or redirect you to fake pages. You should always check the sender’s address, the URL of the link, and the content of the message before clicking on anything. If you are not sure, do not open it or contact the sender to verify.
Use strong and unique passwords for your online accounts. Passwords are the first line of defense against credential stealers. You should use passwords that are long, complex, and different for each account. You can also use a password manager to generate and store your passwords securely.
Enable two-factor authentication (2FA) whenever possible. 2FA adds an extra layer of security to your online accounts by requiring a second factor, such as a code sent to your phone or email, to log in. This way, even if your password is stolen, the attacker cannot access your account without the second factor.
Be careful about what you share online. Some websites and applications may ask you for personal information, such as your name, address, phone number, or social security number. You should only provide this information if you trust the website or application and if it is necessary. You should also review your privacy settings and limit who can see your online activity.
What to do if you shared your information with a scammer?
If you think you’ve become the victim of a scam, contact the Better Business Bureau. You can file a complaint with them 24/7. Besides the BBB, you can also use IdentityTheft.org or call 877-438-4338 if you feel that your identity has been stolen or misused.
Double-check all your financial accounts
If you notice any suspicious activity on your bank accounts or credit card statements, contact your bank and credit card company immediately.
Use Identity theft protection
Identity Theft companies can monitor personal information like your Social Security Number (SSN), phone number, and email address and alert you if it is being sold on the dark web or being used to open an account. They can also assist you in freezing your bank and credit card accounts to prevent further unauthorized use by criminals. The great part of an identity theft company like my #1 pick is that you’re provided with your own personal case manager that will help you recover any losses.
See my tips and best picks on how to protect yourself from identity theft here.
Kurt’s key takeaways
ClearFake and Atomic Stealer are examples of how threat actors are constantly evolving their techniques and expanding their targets. If you use a Mac do not assume that you are immune to malware. You should always be vigilant about the online threats you may encounter.
Have you ever encountered a fake browser update on your Mac? How do you keep your device secure from malware? Let us know in the comments below.
TO GET MORE OF MY SECURITY ALERTS, SUBSCRIBE TO MY FREE CYBERGUY REPORT NEWSLETTER
Answers to the most asked CyberGuy questions:
- What is the best way to protect your Mac, Windows, iPhone, and Android devices from getting hacked?
- What is the best way to stay private, secure, and anonymous while browsing the web?
- How can I get rid of robocalls with apps and data removal services?
Copyright 2023 CyberGuy.com. All rights reserved. CyberGuy.com articles and content may contain affiliate links that earn a commission when purchases are made.


