There is a new Microsoft 365 phishing attack spreading, and it’s been talked about in detail in the latest report from the email security service Vade. Vade’s Threat Intelligence and Response Center (TIRC) was able to gather information about the attack and found that it was being executed using an email with a malicious HTML attachment with JavaScript code. Here’s what we know about the attack and how you can prevent it from finding its way to you.
How does this phishing attack targeting Microsoft 365 work?
The process for the attack begins when someone receives the email mentioned above with the malicious HTML attachment with JavaScript code. If that person opens this attachment, it will open up a phishing page that looks like the person has been logged out of their Microsoft 365 account and needs to log in again to view the file. It is designed to mimic the login interface of Microsoft 365 complete with the logo. Here, the person will be asked to type in their credentials, such as their email address, phone number, or Skype, then their password so that the hackers can steal the authentication information. Once phished, the login credentials are then sent straight to the threat actors.
We reached out to Microsoft for a comment on this phishing attack targeting Microsoft 365 but did not hear back before our deadline for publishing this article.
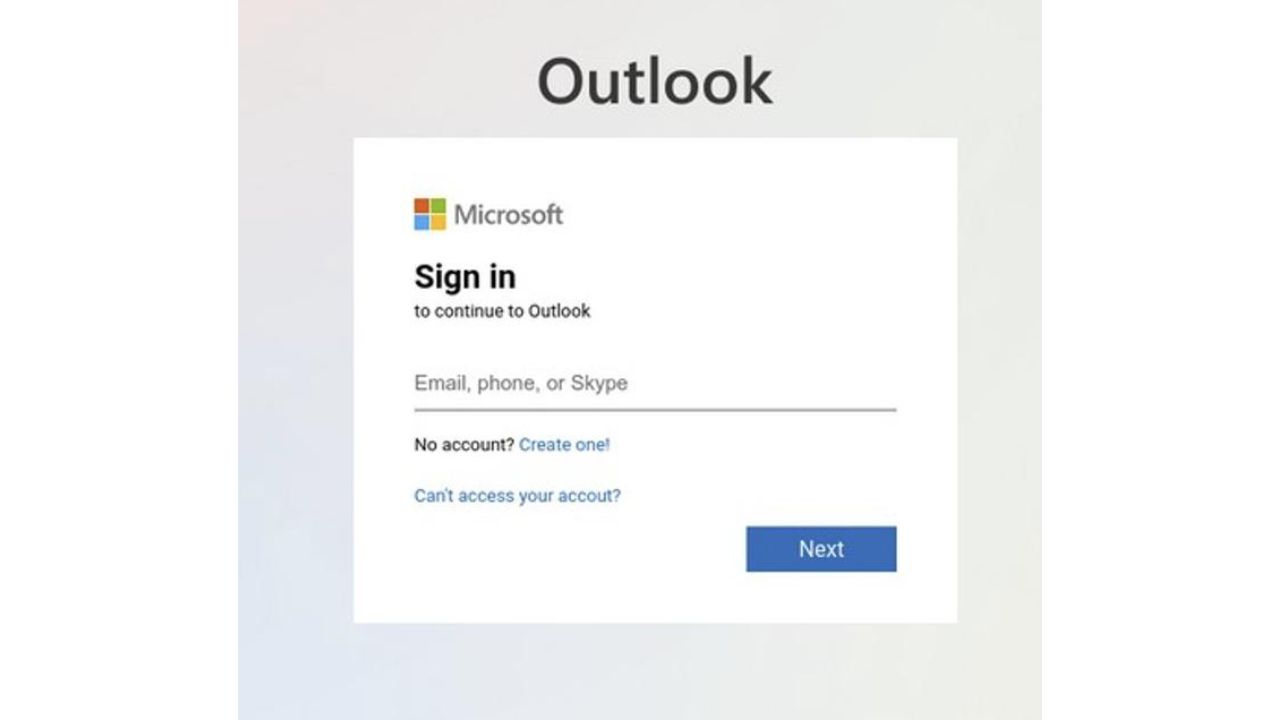
Credit: Vade
Hackers exploit glitch.me to host malicious domain
The hackers have been using the website glitch.me to host these phishing pages, including the malicious domain known as eevilcorponline. Glitch.me is typically used innocently for people to create things like websites and other online projects.
Same team also discovers Adobe phishing attack
While researching the Microsoft 365 phishing attack, the team at Vade also discovered a phishing attack that’s been posing as a legit version of Adobe. Adobe, for those who don’t know, is a renowned software company that specializes in creating multimedia and creativity tools, widely known for products like Photoshop, Illustrator, and Acrobat.
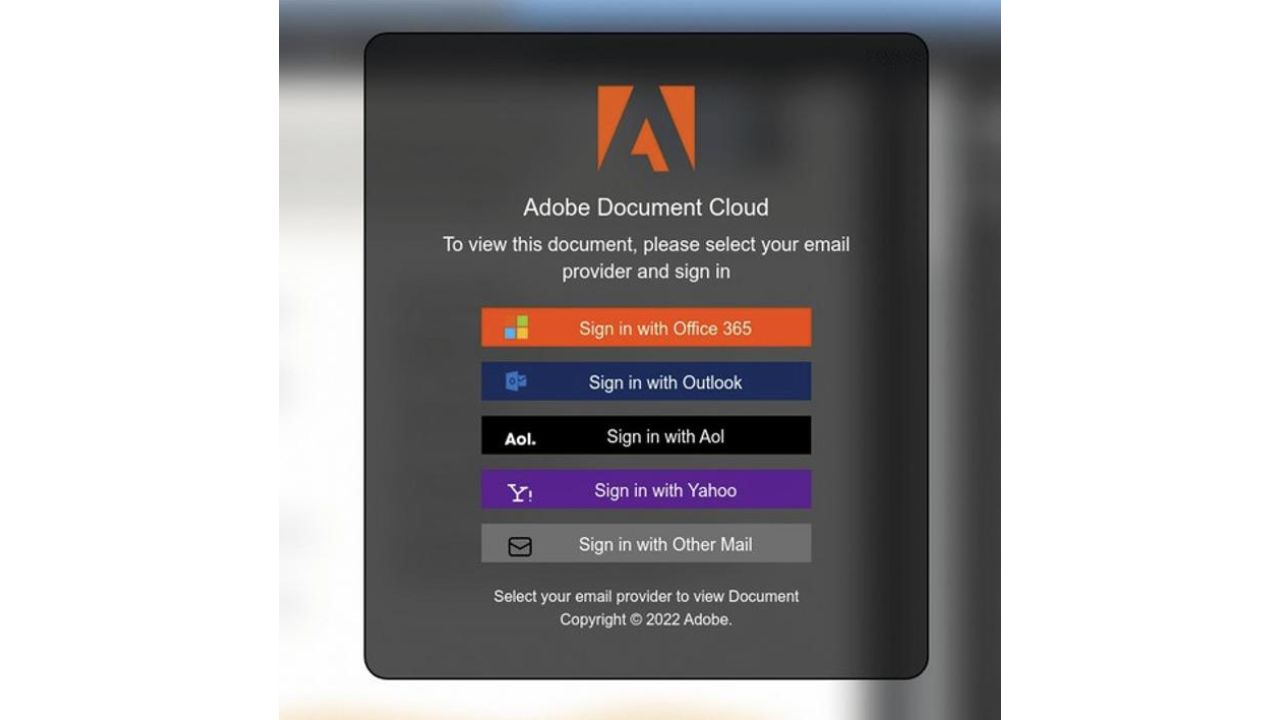
Credit: Vade
Vade found an email pretending to be from Adobe. The email tried to trick people into giving away their personal information. Vade looked at the email and found some secret codes that helped them to understand the scam better. They found a website called “ultimotempore[.]online” that was trying to trick people. They also found another website called “eevilcorp[.]online” that we mentioned earlier that was collecting information about the people who clicked on the scam email.
MORE: NEW MALWARE TARGETING MACOS AND CAN STEAL SENSITIVE INFORMATION FROM YOUR DEVICES
What can I do to protect myself?
Protecting yourself from phishing attacks like the two mentioned above can be intimidating; however, there are a few key signs you can catch on your own as well as services that can help you. Here are some of my tips.
Don’t open any suspicious attachments
If you’re getting an email out of the blue that’s urging you to open an attachment or click on a random link, don’t fall for it. Hackers will often try to use urgency in their emails to make you feel like you have to do what they say, so use your judgment, and if something feels fishy, don’t trust it.
Be cautious of emails asking you to enter your login information
If you receive an email asking you to enter your login information, be cautious. It’s best to go directly to the website in question and log in there rather than clicking on a link in an email.
Use antivirus software
Keeping hackers out of your devices can be prevented if you have good antivirus software installed. Having antivirus software on your devices will make sure you are stopped from clicking on any potential malicious links which may install malware on your devices, allowing hackers to gain access to your personal information.
My #1 pick is TotalAV, and you can get a limited-time deal for CyberGuy readers: $19 your first year (80% off) for the TotalAV Antivirus Pro package.
Double-check the email address
Some hackers will try to pretend to be representatives from bigger companies like Microsoft and Adobe to trick you into thinking they’re legit. Before you click on anything or open any attachments, check the email address of the sender and look it up for yourself. Those bigger companies will have official email addresses, so if this one doesn’t match, you know you’re dealing with a fake.
Kurt’s key takeaways
Phishing attacks are something we’ve talked about often and remain a serious threat and way for cybercriminals to distribute malware. Unfortunately, they won’t be stopping any time soon. However, this doesn’t mean you have to fall victim to them. By following the tips mentioned above, you can protect yourself. So, stay vigilant and keep your guard up against these deceptive schemes to stay one step ahead of these crooks.
Do you feel that security problems are growing or under control? Why do you think it’s often the smaller cybersecurity firms that end up discovering these issues? Let us know by commenting below.
FOR MORE OF MY SECURITY ALERTS, SUBSCRIBE TO MY FREE CYBERGUY REPORT NEWSLETTER HERE
Related:
- Troubling malware threat spreading through Facebook and Twitter
- New malware is targeting macOS and can steal information from your devices
- A new malicious malware is specifically targeting iPhones


