The U.S. Department of Justice just unsealed their indictment charges against Ukrainian national, 26-year-old Mark Sokolovsky. He reportedly infected millions of computers worldwide with malware in an international cybercrime operation the DOJ calls “Raccoon Infostealer.”
Sokolovsky was allegedly a “key administrator” at the operation which at least 50 million unique email addresses, bank accounts, cryptocurrency addresses, credit card numbers were collected and leased to other online criminals for $200 a month.
Learn more about Raccoon Infostealer below and find out how to check if you were one of the millions of worldwide victims.
Table of Contents:
International malware operation infects millions
Dutch authorities arrested Mark Sokolovsky in March 2022, and the FBI then worked with Italy and the Netherlands to dismantle what is called Raccoon Infostealer. They are still working on identifying the exact number but so far over 50 million forms of identification and unique login credentials have appeared to be stolen from victims and according to cybersecurity company Sekoia, Raccoon Stealer 2.0 started being promoted on hacking forums once again starting in June, with the first samples captured by malware analysts earlier this month..
Sokolovsky not only developed the malware, but he did then started charging other online conspirators via cryptocurrency to provide them with the stolen login information he had hacked.
How did the malware get installed on victims’ computers?
The majority of the Raccoon Infostealer malware was installed on devices via phishing emails and links. At the height of the global pandemic, emails were sent posing as a healthcare organization providing information about Covid-19, but the link seen in the email example below actually downloaded Raccoon onto the device when clicked.
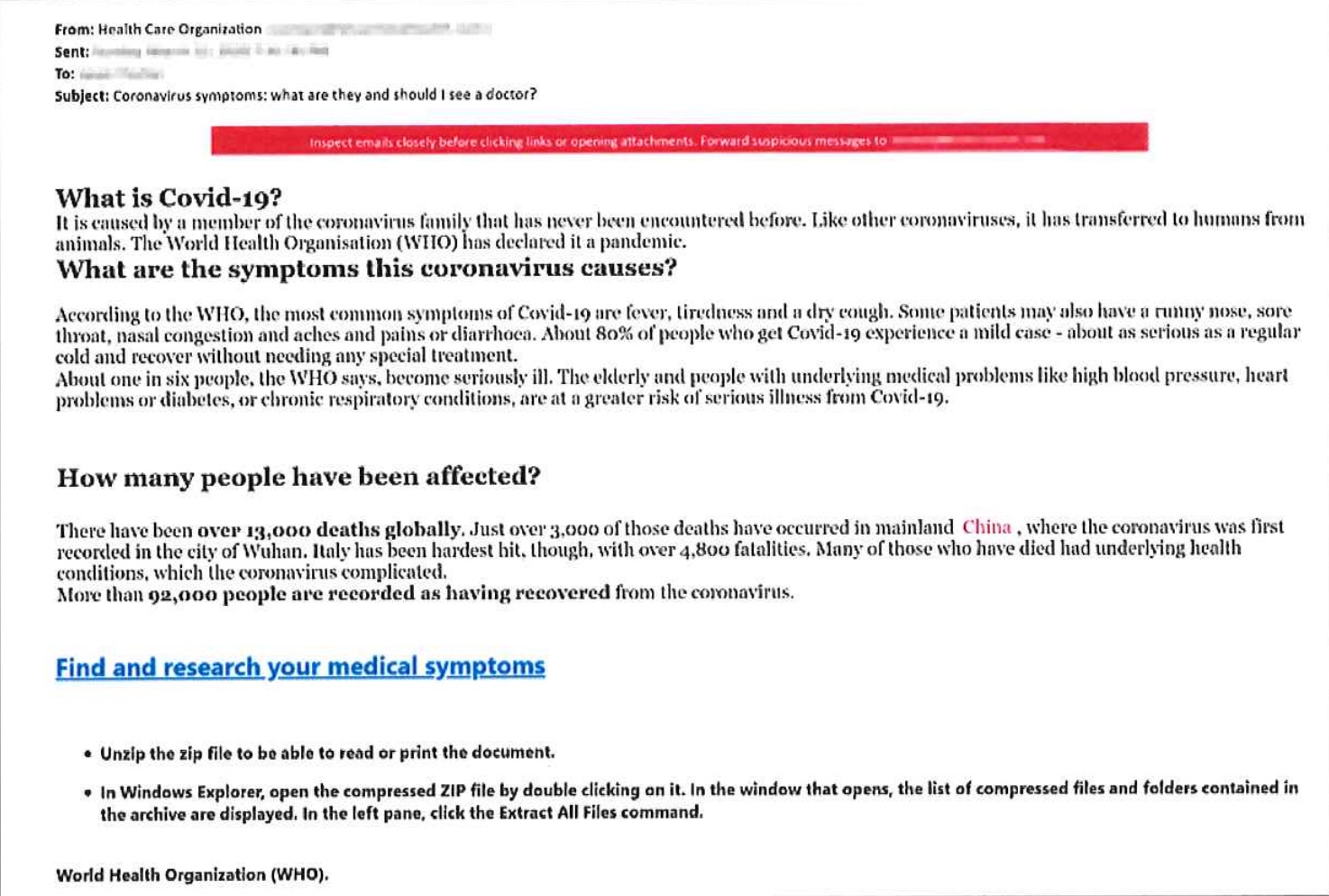
Learn more about preventing phishing attacks here.
What was stolen in the Raccoon Infostealer operation?
Experts have claimed that data breached by this harmful malware may have included:
- Passwords, cookies, autofill data (including saved credit cards)
- Cryptocurrency wallets
- Screenshot captures
- Installed application lists
- System fingerprinting information
How to check if you’ve been targeted
1) Find out if your email has been compromised
The FBI announced they created a website dedicated to checking if you were one of the many global victims of the Raccoon Infostealer.
Visit the Raccoon Infostealer Disclosure page and input your email address to find out if it appears in the FBI’s collected data from the malware hacks. If your email address HAS appeared in the Raccoon Infostealer data, you’ll then receive an email with additional information and resources.
You can always submit information if you believe you’ve been a victim of a cybercrime at the FBI’s Internet Crime Complaint Center (IC3).
Prevent scammers from using your email
Set up an alias email address for all of the websites where you’re required to input your personal information. If that website then ends up selling (or stealing!) your information, you’ll end up with even more emails from people you don’t know. Some of those emails like the ones mentioned in this article can lead to malware.
So all you need to do is delete that email alias! Learn how to create an email alias here.
2) Install an Antivirus software to protect yourself from future attacks
We’ve broken down the top antivirus programs for 2022, but the most important factor to look for if you’re hoping for everyday protection before it’s too late is to find software with trusted real-time monitoring so you don’t even end up installing a malicious app or extension.
Our top recommendation, a premium TotalAV subscription includes both real-time anti-malware protection as well as advanced AI-driven cloud protection, which keeps your computers protected against the very latest zero-day threats.
Should malicious behavior be detected on PC, Mac, Android, and iOS devices, TotalAV interjects and stops the process as well as quarantines the files that are about to cause problems. This process works silently in the background, having minimal impact on system resources.
Once you install the antivirus on your computer, here’s how to scan to remove malware:
While you may hope to protect your devices 24/7 for no cost, any software that offers it for free won’t actually be protecting your devices. Then you may be at a higher risk for viruses and malware because you think your computer or phone is protected.
It’s worth a small price to pay to keep your personal information, data, and all of your devices safe from hackers.


