If you use X, formerly known as Twitter, you might’ve seen grey or gold-verified accounts promoting cryptocurrencies. They often pose as actual cryptocurrencies. While you would think these cryptocurrencies are legitimate — in reality, it’s the work of hackers who hijack X accounts.
These hackers target politicians, companies, and other official accounts that you trust in order to trick you into buying into their crypto-scam. Some act as middlemen, selling accounts to malicious actors.
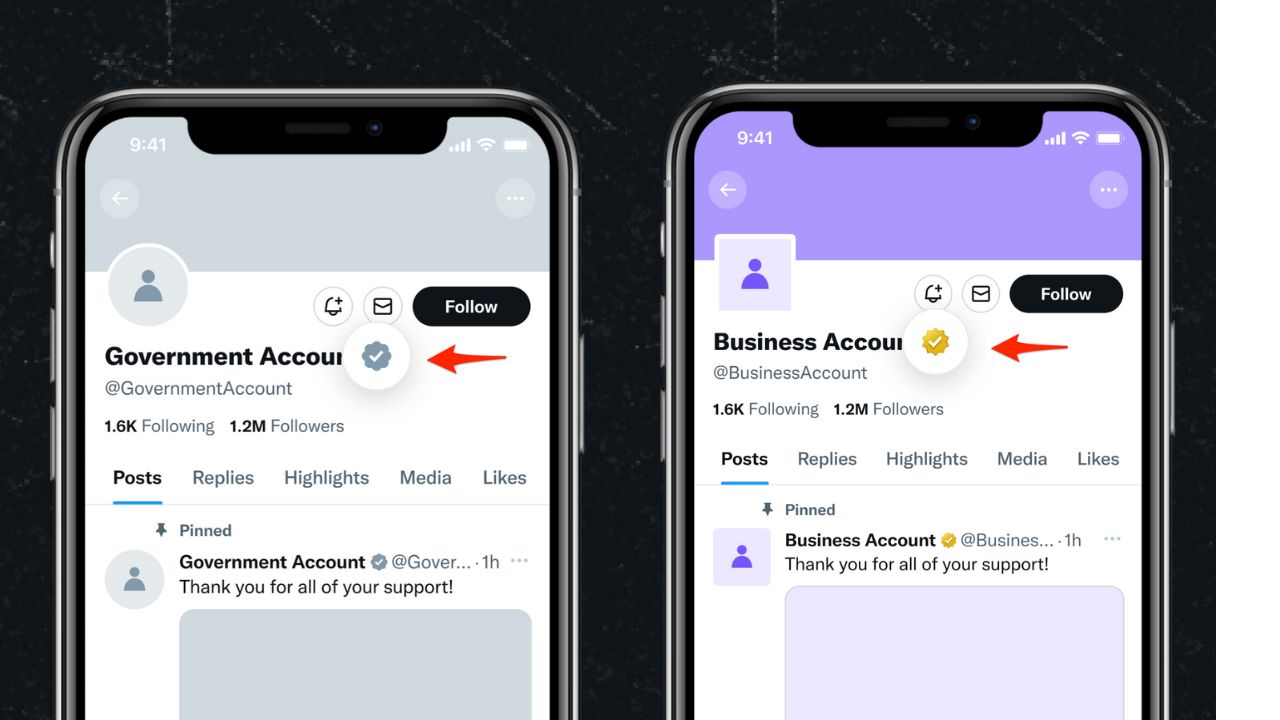
Credit: X Corp.
Using trusted accounts for crypto-scams
Cybersecurity experts MalwareHunterTeam found accounts belonging to a Canadian senator, Brazilian politician, and non-profit all being used to push cryptocurrencies. According to their reports, hackers used that Canadian politician’s account to pose as a legitimate cryptocurrency project, whose actual account isn’t even verified.
That attack is two-fold. Not only are hackers trying to trick X users into thinking that they’re an actual cryptocurrency project — but they also use that gold or grey checkmark to make you think they are trustworthy.
Cybersecurity firm Mandiant also had its X profile taken over. Hackers changed the profile to impersonate the Phantom crypto wallet. They then promised free tokens to users who clicked a link.

Credit: MalwareHunter Team
The screenshot above shows how the attacker used the official Phantom account to retweet posts that warned users to “never rush into clicking links.” This was probably a tactic to make their future crypto-scam posts look more credible.
However, a BleepingComputer report found that users who clicked on the link would get redirected to download the real Phantom cryptocurrency wallet. That’s when hackers would attack — draining unsuspecting users’ crypto wallets.

Credit: MalwareHunter Team
MORE: THE NEW IPHONE SECURITY THREAT THAT ALLOWS HACKERS TO SPY ON YOUR PHONE
How to stay safe on X
Even though these hackers are doing everything they can to trick you into giving them your money, you can take these 10 steps to protect yourself.
1) If it’s too good to be true, then it probably isn’t true
The old adage is usually right. Most hackers hope you don’t see through their schemes and think that you’re getting an incredible deal. However, you have to ask yourself, why would a company just give out free cryptocurrency? Wouldn’t there be a catch? What’s in it for the company?
2) Do your research
Before investing in cryptocurrency, you should make sure you have thoroughly looked into it. Make sure you know what you’re investing in, and you’ve spent ample time researching it. Just clicking on a social media post and trusting it usually isn’t a great idea and can make you a target for hackers.
3) Use a strong password
Use a strong password that you don’t reuse on other websites. Consider using a password manager to generate and store complex passwords. It will help you to create unique and difficult-to-crack passwords that a hacker could never guess. Second, it also keeps track of all your passwords in one place and fills passwords in for you when you’re logging into an account so that you never have to remember them yourself. The fewer passwords you remember, the less likely you will be to reuse them for your accounts.
4) Use two-factor authentication
Two-factor authentication adds an extra layer of security to your X account. When you log in, you need to enter both a password and a verification code or use a security key. This way, only you can access your account. To enroll, you need to have a verified email address linked to your account. X uses your email address to communicate with you and keep your account secure.
Once you turn on this feature, you need two things to log in to your account: your password and a secondary verification method. You can choose from a code, an app confirmation, or a physical security key.
5) Require email and phone number to request a reset password link or code
Having an up-to-date email address attached to your account is a great way to improve your account security. Also, adding a phone number to your account is a great step to keep your account secure. With a phone number on your account, you’ll be able to enroll in security features like login verification. It will also allow for faster account recovery. If you ever lose access to your account, having a phone number attached can make it easier for you to get back into your X account.
6) Be cautious of suspicious links
Be cautious of suspicious links, and always make sure you’re on twitter.com before you enter your login information.
7) Don’t fall for fake promises
Never give your username and password out to third parties, especially those promising to get you followers, make you money, or verify you.
8) Make sure your software is updated
Make sure your computer software, including your browser, is up-to-date with the most recent upgrades and anti-virus software.
9) Have good antivirus software on all your devices
The best way to protect yourself from having your data breached is to have antivirus protection installed on all your devices. Having good antivirus software actively running on your devices will alert you of any malware in your system, warn you against clicking on any malicious links in phishing emails, and ultimately protect you from being hacked.
Special for CyberGuy Readers: My #1 pick is TotalAV, and you can get a limited-time deal for CyberGuy readers: $19 your first year (80% off) for the TotalAV Antivirus Pro package.
10) Check to see if your account has been compromised
If you really think your X account has been hacked, then you should check to see if your account has been compromised. You can do this by visiting the Security and Login section of your account settings and reviewing the devices and locations where you have logged in. If you see any suspicious activity, such as logins from unknown devices or locations, you should immediately change your password and enable two-factor authentication. You should also report any unauthorized access to X.
Credit: X Corp.
If you suspect you’re a victim of a social media scammer
If you suspect you’re a victim of a social media scammer, you need to take urgent action immediately. Here are some immediate steps to take:
Secure your account
Immediately change your password to lock potential hackers out. If you’re locked out of your account, contact X’s support immediately to recover it.
Inform your contacts
Let your friends and family know so they’re aware. That way, hackers won’t dupe them with messages or requests coming from your compromised account.
Monitor account activities
Keep an eye on your active sessions, messages sent, and any changes made to your account. You should try to report and reverse any unfamiliar activity.
Seek expert help
If you believe your personal information, such as financial data or other sensitive details, has been compromised, consider reaching out to cybersecurity professionals or services. They can guide you on further recovery and protection steps.
Use identity theft protection
If you want a service that will walk you through every step of the reporting and recovery process, one of the best things you can do to protect yourself from this type of fraud is to subscribe to an identity theft service
Theft protection companies can monitor personal information like your home title, Social Security Number (SSN), phone number, and email address. They can also alert you if it is on sale on the dark web or if someone is using it to open an account. They can also assist you in freezing your bank and credit card accounts to prevent further unauthorized use by criminals.
One of the best parts of using some services is that they might include identity theft insurance of up to 1 million dollars to cover losses and legal fees and a white glove fraud resolution team where a US-based case manager helps you recover any losses.
See my tips and best picks on how to protect yourself from identity theft
MORE: HOW TO OUTSMART CRIMINAL HACKERS BY LOCKING THEM OUT OF YOUR DIGITAL ACCOUNTS
Kurt’s key takeaways
These hackers are trying to take advantage of your trust and hope you let your guard down. That’s why it’s so important to be vigilant. While they are trying to fool you with official-looking accounts, try to verify them using the person or organization’s website or other social media accounts. While X’s grey and gold verification marks are usually legitimate, they’re not 100 percent foolproof.
What do you think X or other social media platforms should do to prevent or stop crypto scams? Let us know in the comments below.
FOR MORE OF MY SECURITY ALERTS, SUBSCRIBE TO MY FREE CYBERGUY REPORT NEWSLETTER HERE
Copyright 2024 CyberGuy.com. All rights reserved. CyberGuy.com articles and content may contain affiliate links that earn a commission when purchases are made.
🛍️ SHOPPING GUIDES:
KIDS | MEN | WOMEN | TEENS | PETS |
FOR THOSE WHO LOVE:
COOKING | COFFEE | TOOLS | TRAVEL | WINE |
DEVICES:
LAPTOPS | TABLETS | PRINTERS | DESKTOPS | MONITORS | EARBUDS | HEADPHONES | KINDLES | SOUNDBARS | KINDLES | DRONES |
ACCESSORIES:
CAR | KITCHEN | LAPTOP | KEYBOARDS | PHONE | TRAVEL | KEEP IT COZY |
PERSONAL GIFTS:
PHOTOBOOKS | DIGITAL PHOTO FRAMES |
SECURITY
ANTIVIRUS | VPN | SECURE EMAIL |
CAN'T GO WRONG WITH THESE:



