Hackers are always finding new ways to break into your devices. A troubling new vulnerability in iOS now allows hackers to spy on you through your keyboard. Certo Software released a report revealing how cybercriminals are avoiding Apple’s stringent security measures to steal your information.
Essentially what hackers are doing is installing a third-party keyboard that features a keylogger into your iPhone. They’ll disguise that keylogger in a small app and use Apple’s TestFlight tool for app developers to bypass Apple’s security checks. Hackers are hoping you download those apps and turn over your own information.
What is TestFlight?
Developers need a place to test their apps, and TestFlight provides a space for that. It lets developers upload unfinished versions of apps and send out links to testers. They have a range of testing options too. Developers can have testers tinker with the whole app or create “App Clips” or specific test features. Testers have the option to test the whole app or “App Clips” and provide feedback to both the developer and Apple.
Credit: Apple
It’s Apple’s top developer tool. Many of the reviews cite how easy it is to use and how it makes beta testing a breeze. There are some security concerns, however. Apple shares your name and email if you use the app. If you’re a tester, it shares the type of device you’re using, carrier, and other information.
MORE: BEWARE OF FAKE BROWSER UPDATES ON YOUR MAC
How are hackers using TestFlight to steal your information?
Certo notes that hackers use a fairly straightforward practice. They’ll install a small app containing a custom keyboard. That keyboard features a keylogger, which records everything you type and transmits to them. Once the app is installed on your phone, they’ll install the custom keyboard on your iPhone through your settings app and give the keyboard full access.
They’ll then switch your keyboard from the default one to their malicious version. It’s important to note that oftentimes, these keyboards will look virtually identical to the iPhone’s default keyboard — which makes it nearly impossible to tell if you’re using a compromised keyboard.

MORE: HOW TO PROTECT YOUR IPHONE FROM CYBERATTACKS WITH LOCKDOWN MODE
How you can protect yourself
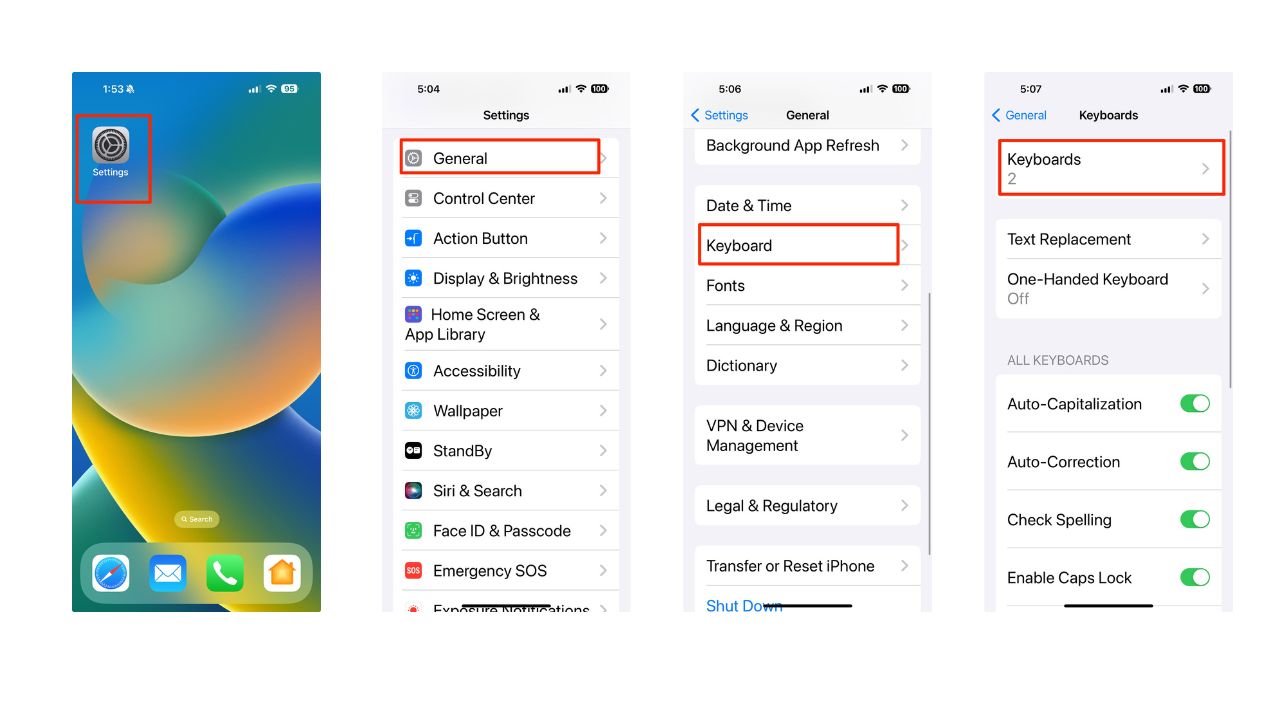
To make sure you’re not using a compromised keyboard, you should check your keyboard settings in iOS. Here’s how you can check:
- Head to your Settings app
- Click General
- Select Keyboard
- Then click Keyboards
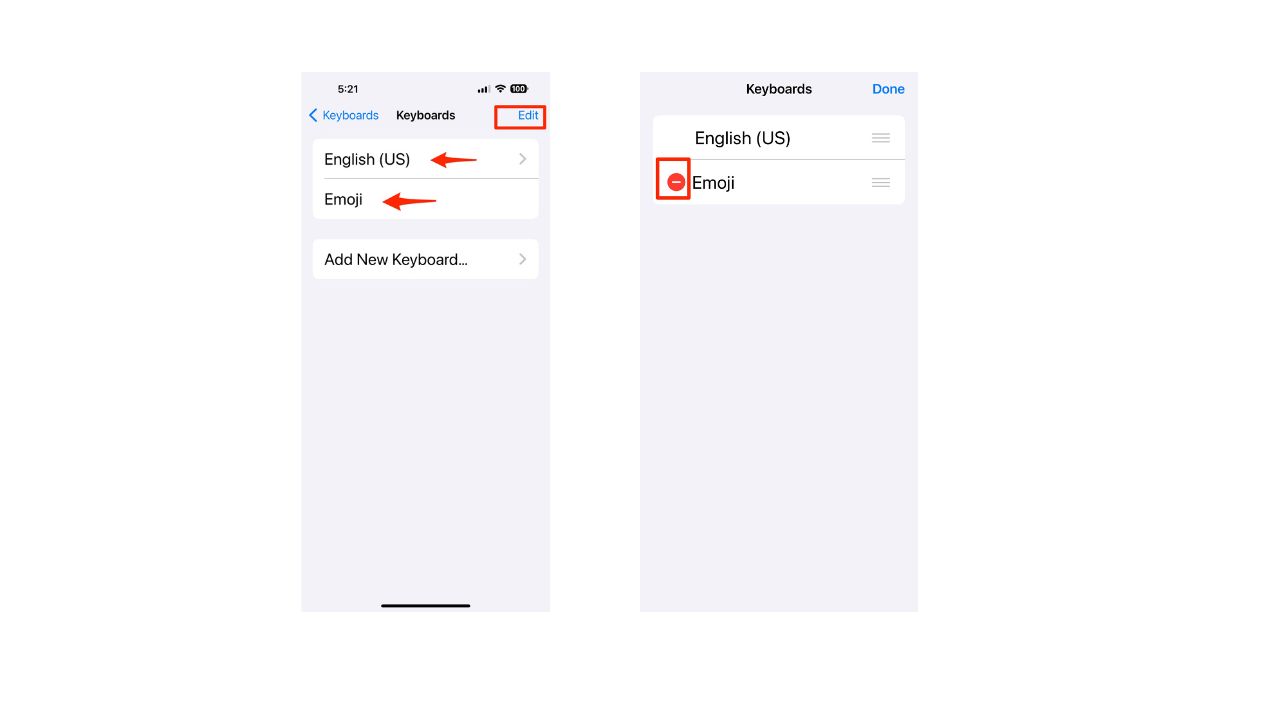
- You should see which keyboards you’re using. In this example, you see both English (US) and Emoji. If you tap on English (US) you will see QWERTY, AZERTY, QWERTZ, and Dvorak. They are all standard keyboard layouts that are built-in to iOS. They are not third-party keyboards and they are safe to use.
- If you see a keyboard you don’t recognize or want to delete it, click on Edit
- Then click on the red minus sign in front of the keyboard (The emoji app is legit. We used it as an example of how to delete a third-party keyboard)
MORE: POLICE URGE PARENTS TO TURN OFF APPLE IPHONE SETTING DANGEROUS TO KIDS
How to protect your iPhone from keyboard spying attacks
Avoid downloading apps from unknown or untrusted sources. Only download apps from the official App Store or from reputable developers.
Be careful when using TestFlight to test apps. Read the app description and reviews carefully before installing. Do not grant full access to any custom keyboards that you do not recognize or trust.
Check your keyboard settings regularly and delete any suspicious or unwanted keyboards. You can follow the steps we outline above to do this.
Update your iOS to the latest version and install any security patches that Apple releases. This can help fix any vulnerabilities or bugs that hackers might exploit.
Have good antivirus software on all your devices. Keeping hackers out of your devices can be prevented if you have good antivirus software installed. Having antivirus software on your devices will make sure you are stopped from clicking on any potential malicious links that may install malware on your devices, allowing hackers to gain access to your personal information.
Special Holiday Deal for CyberGuy Readers: My #1 pick is TotalAV, and you can get a limited-time deal for CyberGuy readers: $14.95 your first year (85% off) for the TotalAV Antivirus Pro package. Deal exp. 12/15.
Find my review of Best Antivirus Protection here
What should you do if you are a victim of a keyboard spying attack
If it has already happened, then you should take immediate action to minimize the damage and secure your device. Here are some steps that you can follow:
1. Change your passwords. If hackers have recorded your passwords using the keylogger, they could access your online accounts and steal your data or money. ON ANOTHER DEVICE (i.e., your laptop or desktop), you should change your passwords for all your important accounts, such as email, banking, social media, etc. You want to do this on another device so the hacker isn’t’ recording you setting up your new password on your hacked deviceUse strong and unique passwords that are hard to guess or crack. You can also use a password manager to generate and store your passwords securely.
2. Monitor your accounts and transactions. You should check your online accounts and transactions regularly for any suspicious or unauthorized activity. If you notice anything unusual, report it to the service provider or the authorities as soon as possible. You should also review your credit reports and scores to see if there are any signs of identity theft or fraud.
3. Contact your bank and credit card companies. If hackers have obtained your bank or credit card information, they could use it to make purchases or withdrawals without your consent. You should contact your bank and credit card companies and inform them of the situation. They can help you freeze or cancel your cards, dispute any fraudulent charges, and issue new cards for you.
4. Alert your contacts. If hackers have accessed your email or social media accounts, they could use them to send spam or phishing messages to your contacts. They could also impersonate you and ask for money or personal information. You should alert your contacts and warn them not to open or respond to any messages from you that seem suspicious or unusual.
5. Restore your device to factory settings. If you want to make sure that your device is completely free of any malware or spyware, you can restore it to factory settings. This will erase all your data and settings and reinstall the original iOS version. You should back up your important data before doing this, and only restore it from a trusted source.
6. Use identity theft protection: If hackers were to record everything you type on your keyboard they could use this information to open accounts in your name, access your bank and credit card accounts, and impersonate you online. That’s where Identity Theft protection companies come in. They can monitor personal information like your home title, Social Security Number (SSN), phone number, and email address and alert you if it is being used to open an account. They can also assist you in freezing your bank and credit card accounts to prevent further unauthorized use by criminals. See my tips and best picks on how to protect yourself from identity theft.
Kurt’s key takeaways
There are hundreds, if not thousands, of ways hackers can steal your information. You can do yourself a favor by giving them one less avenue to hack you by being careful about where you download your apps and keeping an eye out for malicious software.
Do you think tech companies like Apple should take additional measures to protect you from potential security breaches, or do you believe it’s primarily your responsibility to safeguard your devices? Let us know what you think in the comments below.
FOR MORE OF MY TECH TIPS & SECURITY ALERTS, SUBSCRIBE TO MY FREE CYBERGUY REPORT NEWSLETTER HERE
Answers to the most asked CyberGuy questions:
- What is the best way to protect your Mac, Windows, iPhone, and Android devices from getting hacked?
- What is the best way to stay private, secure, and anonymous while browsing the web?
- How can I get rid of robocalls with apps and data removal services?
Copyright 2023 CyberGuy.com. All rights reserved. CyberGuy.com articles and content may contain affiliate links that earn a commission when purchases are made.
🛍️ SHOPPING GUIDES:
KIDS | MEN | WOMEN | TEENS | PETS |
FOR THOSE WHO LOVE:
COOKING | COFFEE | TOOLS | TRAVEL | WINE |
DEVICES:
LAPTOPS | TABLETS | PRINTERS | DESKTOPS | MONITORS | EARBUDS | HEADPHONES | KINDLES | SOUNDBARS | KINDLES | DRONES |
ACCESSORIES:
CAR | KITCHEN | LAPTOP | KEYBOARDS | PHONE | TRAVEL | KEEP IT COZY |
PERSONAL GIFTS:
PHOTOBOOKS | DIGITAL PHOTO FRAMES |
SECURITY
ANTIVIRUS | VPN | SECURE EMAIL |
CAN'T GO WRONG WITH THESE:




1 comment
I believe Apple should always make sure security is of high importance and keep the Apple products that we purchase from them safe from hackers! We pay more for the Apple product therefore we are relying on them to keep us safe from any breach! Otherwise we could purchase other name brand products and just purchase extra protection!! We purchase Apple products because we believe they are superior and safer!!!!!
I hope that is still the case!