Share this article with anyone who may find this helpful!
Subtle updates we make to social media are all clues for malicious actors to work against you – and your company.
Every ‘like’ you tap on Facebook, a link to your resume at a job site, every photo shared on Instagram; it’s all a treasure trove for cyber criminals.
Hackers are now using powerful AI software to scan posts made everywhere in social media. It can harvest the smallest details about your life in minutes. I spoke with a renowned 25 year veteran of cyber security, David Melnick, who says he’s watching how online criminal rings are now getting more effective, more dangerous, and more able to find rich targets.
“With the advent of AI and machine learning they can now scan millions of profiles and anyone that happens to be particularly vulnerable where they find something, that can be when they begin a more targeted attack,” according to Melnick.
Jump down to: Best Antivirus Software and Apps to Protect Against Malware

The most effective is a spear phishing attack. It’s a fake-out sent to you in the form of a legit-looking email with tones of familiarity designed to trick you into clicking a link.
For example, you post a photo from a meal out at a restaurant celebrating the moment. A caption might read.. ‘Loved dinner at Dusty’s Diner with friends’.
Even without that sophisticated help, you can learn enough about someone through social media in less than 30 minutes in order to pose a serious threat. This is why it’s so important that you are protecting mobile devices and computers.
A hacker accessing your restaurant post targets you with an email like this:
‘Hey, thanks so much for dining with us at Dusty’s. I’m the GM and just want to say thank you personally. We’d love to see you and your friends again soon, please enjoy this link to a 20% discount good for your next visit. Thanks again! It was great to have you with us!’

Instead of a discount, the link is a trick that leads you into inadvertently installing malware without you knowing it’s a hacker fake-out. Now that malware is invisibly sharing everything on your screen and everything you type to a criminal hacking ring.
Jump down to: Best AntiVirus Software and Apps to Protect Against Malware
As more and more people return to work, they are eagerly taking spontaneous selfies with office colleagues. In those shared photos are often compromising details such as the company’s security id hanging around necks or clipped onto clothing shown in the photos.
Hackers are also able to enhance items in the photo’s background like work computer screens and post-it notes. These can be used to further confirm the identity of others, impersonate an employee, and target the company or co-workers in this new intimate form of hacking.
Criminals are good at it. Since it’s working, criminals are investing in expensive tools to help with the scams.

“Just like companies today are using A.I. to make their systems better, the adversaries we fight here are making substantial investments in improving the quality of their techniques, the efficiencies, the speed.” David Melnick, with his 25 years of hands-on cyber security experience goes on to say, “And so a machine learning based system is one great example of how they are honing their craft.”
There are some actions you can take to help block these social media-sourced attacks and also check to see if you have already been scammed into downloading an identifiable malware threat.
How to outsmart social media hackers
- Pick unique profile pictures for each social network so that it’s more difficult for hackers to use one photo to find you on all the others.
- Re-examine your privacy settings on all social networks. Maybe even remove ghost followers with an app from your social media accounts.
- Think like a hacker before you post.
- Avoid sharing your company email address in social media.
- Use Malware Detection security protection software and apps
How to spot malicious emails
- When you look closely at the sender’s email address, it’s not correct.
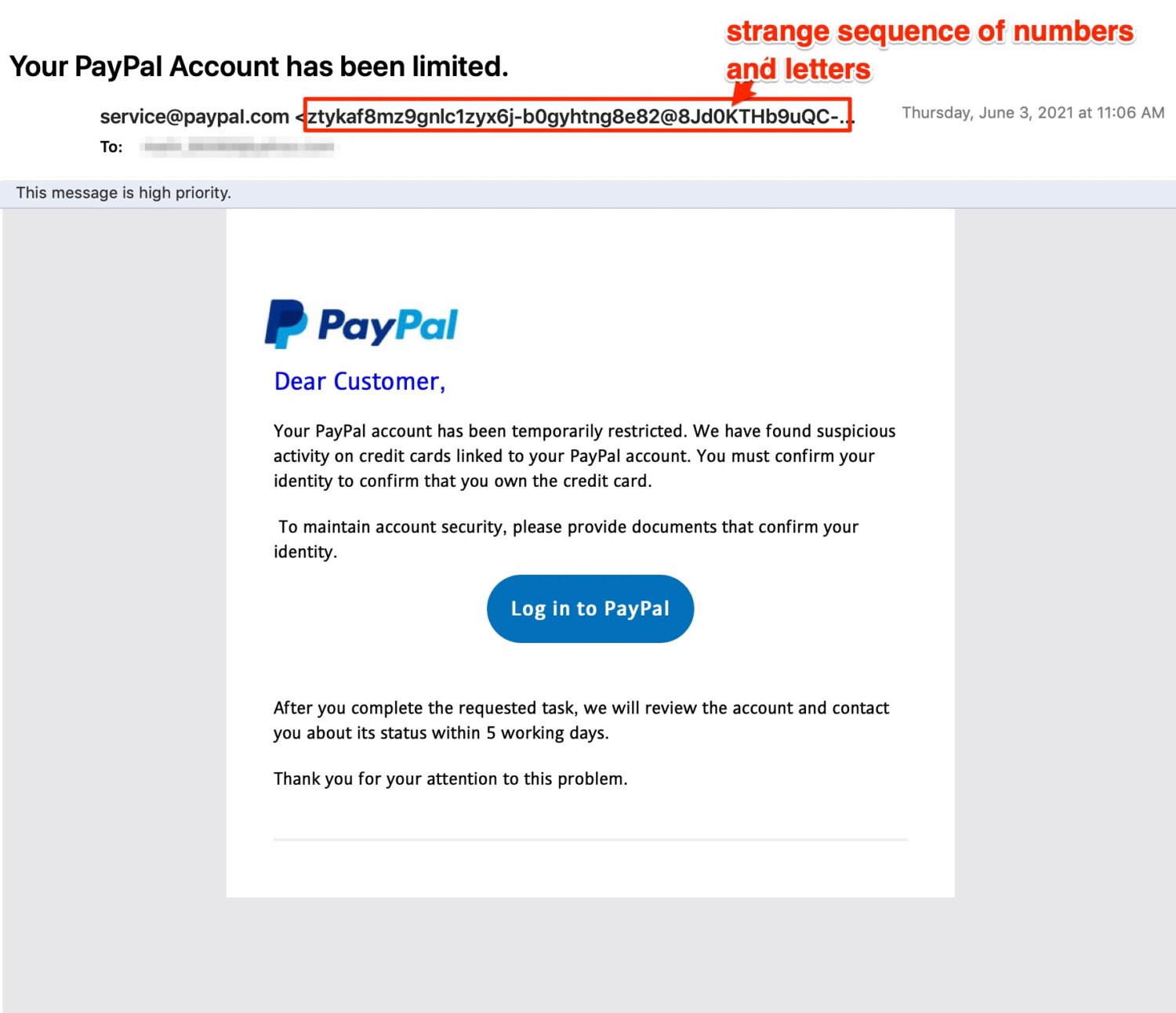
- Something about the tone is slightly off. At first glance, it may seem right, but take a beat longer with a skeptical eye, and you see something not as expected.
- Hover over a link or email address without clicking to see if it looks off. Such as added characters or numbers.
- Links in the email may show a misspelled or strange web address. Such as “TrustedSiteName-02920423.com”
- Most companies do not ever send email asking for credentials.
- When you encounter a call-to-action link or button, let that raise a red flag. It means someone could be phishing for personal information to compromise your security.
- If you should ever get an email like this, never click on any links. If you want to double-check, again, don’t click on any links in the email but instead, open up a new browser and type in the company web address and log into your account. If the email you just received is true, the information should be reflected in your account. Odds are, the email you just received is malicious and you should mark it as “junk” or delete it.
What to do if you think you may have clicked on a malicious link
Use trusted anti-virus security software or apps to scan your device for a previous attack. Malware can be placed on your device unknowingly. Hackers spend day and night thinking of ways to trick you. If these criminals weren’t succeeding, I would not be sharing these important links below to some of the most powerful tools to use for detecting malware.
Best Antivirus Software and Apps to protect against malware
One of the top anti-virus apps for Macs, Windows, Android phones and iPhones is TotalAV. Their product is full of features to keep you safe from malware and protect you when browsing the internet including ransomware protection, real-time antivirus protection, elimination of viruses and malware, a tool to free up your computer’s space, plus more. Limited time deal for CyberGuy readers: $19 your first year (80% off)
You can check out our review of other anti-virus apps, here: Best Antivirus Security Software and Apps to Protect You
No matter what protection you decide to use, awareness is half the battle. Keep second and third guessing every suspicious sense you feel in your gut when engaged in technology, reading email and texts.
Share this with anyone who may find this helpful by clicking the share button at the top of this article.
More ways to take back your privacy:
- Best VPNs for Browsing the Internet Privately
- Best Alternatives to Big Tech Beast Google
- Map buried inside your phone reveals where you have been and photos you snapped there
- How to Give Ring a Quick Privacy Checkup
- Don’t make this one mistake when getting rid of your old phone
- Working from Home? How Your Boss May Be Watching You
- Real-life Spy Catcher Sweeps My House and Finds Everything
🛍️ SHOPPING GUIDES:
KIDS | MEN | WOMEN | TEENS | PETS |
FOR THOSE WHO LOVE:
COOKING | COFFEE | TOOLS | TRAVEL | WINE |
DEVICES:
LAPTOPS | TABLETS | PRINTERS | DESKTOPS | MONITORS | EARBUDS | HEADPHONES | KINDLES | SOUNDBARS | KINDLES | BLUETOOTH SPEAKERS | DRONES |
ACCESSORIES:
CAR | KITCHEN | LAPTOP | KEYBOARDS | PHONE | TRAVEL | KEEP IT COZY |
PERSONAL GIFTS:
PHOTOBOOKS | DIGITAL PHOTO FRAMES |
SECURITY
ANTIVIRUS | VPN | SECURE EMAIL |
CAN'T GO WRONG WITH THESE:




2 comments
Do you need (example) Bitdefender Total Security and a VPN to be secure?
Thanks, Ron
Great question. The short answer is yes – the antivirus program keeps your devices safe from threats like malware, while the VPN protects your data via encryption and hides your online activities.